How to decrypt or get back encrypted files infected by known encrypting ransomware viruses.
In the last years, cybercriminals distribute a new type of viruses that can encrypt files on your computer (or your network) with the purpose of earning easy money from their victims. This type of viruses are called “Ransomware” and they can infect computer systems if the computer's user doesn’t pay attention when opening attachments or links from unknown senders or sites that have been hacked by cybercriminals. According to my experience, the only safe way to keep oneself protected from this type of viruses, is to have clean backups of your files stored in a separate place from your computer. For example, in an unplugged external USB hard drive or in DVD-Rom’s.
This article contains important information of some known encrypting ransomware –crypt- viruses that were designed to encrypt critical files plus the available options & utilities in order to decrypt your encrypted files upon infection. I wrote this article in order to keep all the information for the available decrypt tools in one place and I will try to keep this article updated. Please share with us your experience and any other new information you may know in order to help each other.
How to decrypt files encrypted from Ransomware – Description & Known Decryption Tools – Methods:
- RANSOWARE NAME
- Cryptowall
- CryptoDefense & How_Decrypt
- Cryptorbit or HowDecrypt
- Cryptolocker (Troj/Ransom-ACP”, “Trojan.Ransomcrypt.F)
- CryptXXX V1, V2, V3 (Variants: .crypt , crypz, or 5 hexadecimal characters)
- Locky & AutoLocky (Variants: .locky)
- Trojan-Ransom.Win32.Rector
- Trojan-Ransom. Win32.Xorist, Trojan-Ransom.MSIL.Vandev
- Trojan-Ransom.Win32.Rakhni
- Trojan-Ransom.Win32.Rannoh or Trojan-Ransom.Win32.Cryakl.
- TeslaCrypt (Variants: .ecc, .ezz, .exx, .xyz, .zzz,. aaa, .abc, .ccc, & .vvv)
- TeslaCrypt 3.0 (Variants: .xxx, .ttt, .micro, .mp3)
- TeslaCrypt 4.0 (Filename & Extension unchanged)
Updates June 2016:
1. Trend Micro has released a Ransomware File Decryptor tool to attempt to decrypt files encrypted by the following ransomware families:
CryptXXX V1, V2, V3* <original filename>.crypt , crypz, or 5 hexadecimal characters
CryptXXX V4, V5 <MD5 Hash>.5 Hexadecimal Characters
TeslaCrypt V1 <original filename>.ECC
TeslaCrypt V2 <original filename>.VVV, CCC, ZZZ, AAA, ABC, XYZ
TeslaCrypt V3 <original filename>.XXX or TTT or MP3 or MICRO
TeslaCrypt V4 <original filename>.<original extension>
SNSLocker <original filename>.RSNSLocked
AutoLocky <original filename>.locky
BadBlock <Original file name>
777 <Original file name>.777
XORIST <original filename>.xorist or random extension
XORBAT <original filename>.crypted
CERBER V1 <10 Random Characters>.cerber
Stampado <original filename>.locked
Nemucod <original filename>.crypted
Chimera <original filename>.crypt
* Note: Applies to CryptXXX V3 ransomware: Due to the advanced encryption of this particular Crypto-Ransomware, only partial data decryption is currently possible on files affected by CryptXXX V3, and you have to use a thrird party repair tool to repair your files like: http://www.stellarinfo.com/file-repair/file-repair-toolkit.php
To download Trend Micro’s Ransomware File Decrypter tool (and read the instructions on how to use it), navigate to this page: Downloading and Using the Trend Micro Ransomware File Decryptor
2. Kasperky has released the following decryptor tools:
A. Kaspersky's RakhniDecryptor tool is designed to decrypt files affected by*:
* Note: RakhniDecryptor utility is always updated to decrypt files from several ransomware families.
Rakhni
Agent.iih
Aura
Autoit
Pletor
Rotor
Lamer
Lortok
Cryptokluchen
Democry
Bitman – TeslaCrypt version 3 and 4B. Kaspersky's RannohDecryptor tool is designed to decrypt files affected by:
Rannoh
AutoIt
Fury
Crybola
Cryakl
CryptXXX versions 1 and 2
Cryptowalll – Virus Information & Decryption Options.
The Cryptowall (or “Cryptowall Decrypter”) virus is the new variant of Cryptodefense ransomware virus. When a computer is infected with Cryptowall ransomware, then all the critical files on the computer (including the files on mapped –network- drives if you're logged in a network) become encrypted with strong encryption, that makes it practically impossible to decrypt them. After the Cryptowall encryption, the virus creates and sends the private key (password) to a private server in order to be used from the criminal to decrypt your files. After that, the criminals inform their victims that all their critical files are encrypted and the only way to decrypt them is to pay a ransom of 500$ (or more) in a defined time period, otherwise the ransom will be doubled or their files will be lost permanently.
How to decrypt Cryptowall infected files and get your files back:
If you want to decrypt Cryptowall encrypted files and get your files back, then you have these options:
A. The first option is to pay the ransom. If you decide to do that, then proceed with the payment at your own risk because according to our research some users get their data back and some others don’t. Keep in mind that criminals are not the most trustworthy people in the planet.
B. The second option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
C. If you don’t have a clean backup, then the only option that remains is to restore your files in previous versions from “Shadow Copies”. Observe that this procedure works only in Windows 8, Windows 7 and Vista OS and only if the “System Restore” feature was previously enabled on your computer and was not disabled after the Cryptowall infection.
- Referral link: How to restore your files from Shadow Copies.
A detailed analysis of Cryptowall ransomware infection and removal can be found in this post:
CryptoDefense & How_Decrypt – Virus Information & Decryption.
Cryptodefense is another ransomware virus that can encrypt all the files on your computer regardless of their extension (file type) with strong encryption so that it makes it practically impossible to decrypt them. The virus may disable the “System Restore” feature on the infected computer and may delete all “Shadow Volume Copies” files, so you cannot restore your files to their previous versions. Upon infection Cryptodefense ransomware virus, creates two files on every infected folder (“How_Decrypt.txt” and “How_Decrypt.html”) with detailed instructions on how to pay the ransom in order to decrypt your files and sends the private key (password) to a private server in order to be used by the criminal to decrypt your files.
A detailed analysis of Cryptodefense ransomware infection and removal can be found in this post:
How to decrypt Cryptodefense encrypted files and get your files back:
In order to decrypt Cryptodefense infected files you have these options:
A. The first option is to pay the ransom. If you decide to do that, then proceed with the payment at your own risk because according to our research, some users get their data back and some others don’t. Keep in mind that criminals are not the most trustworthy people in the planet.
B. The second option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
C. If you don’t have a clean backup then you can try to restore your files in previous versions from “Shadow Copies”. Observe that this procedure works only in Windows 8, Windows 7 and Vista OS and only if the “System Restore” feature was previous enabled on your computer and was not disabled after the Cryptodefense infection.
- Referral link: How to restore your files from Shadow Copies.
D. Finally, if you don’t have a clean backup and you aren’t able to restore your files from “Shadow Copies”, then you can try to decrypt Cryptodefense’s encrypted files by using the Emsisoft’s Decryptor utility. To do that:
Important Notice: This utility works only for computers infected before 1st April 2014.
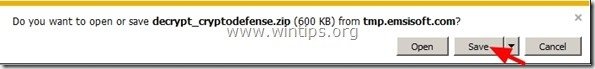
1. Download “Emsisoft Decrypter” utility to your computer (e.g. your Desktop).
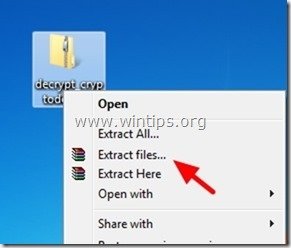
2. When download is completed, navigate to your Desktop and “Extract” the “decrypt_cryptodefense.zip” file.
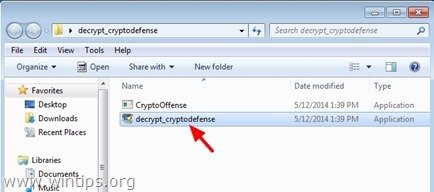
3. Now double-click to run the “decrypt_cryptodefense” utility.
4. Finally press the “Decrypt” button to decrypt your files.
Source – Additional information: A detailed tutorial on how to decrypt CryptoDefense encrypted files using Emsisoft’s decrypter utility can be found here: http://www.bleepingcomputer.com/virus-removal/cryptodefense-ransomware-information#emsisoft
Cryptorbit or HowDecrypt – Virus Information & Decryption.
Cryptorbit or HowDecrypt virus is an ransomware virus that can encrypt all the files on your computer. Once your computer is infected with Cryptorbit virus all your critical files are encrypted regardless of their extension (file type) with strong encryption that makes it practically impossible to decrypt them. The virus also creates two files on every infected folder on your computer (“HowDecrypt.txt” and “HowDecrypt.gif”) with detailed instructions on how you can pay the ransom and decrypt your files.
A detailed analysis of Cryptorbit ransomware infection and removal can be found in this post:
How to decrypt Cryptorbit infected files and get your files back:
In order to decrypt Cryptorbit encrypted files you have these options:
A. The first option is to pay the ransom. If you decide to do that, then proceed with the payment at your own risk because according to our research some users get their data back and some others don’t.
B. The second option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
C. If you don’t have a clean backup, then you can try to restore your files in previous versions from “Shadow Copies”. Observe that this procedure works only in Windows 8, Windows 7 and Vista OS and only if the “System Restore” feature was previous enabled on your computer and was not disabled after the Cryptorbit infection.
- Referral link: How to restore your files from Shadow Copies.
D. Finally, if you don’t have a clean backup and you aren’t able to restore your files from “Shadow Copies” then you can try to decrypt Cryptorbit’s encrypted files by using the Anti-CryptorBit utility. To do that:
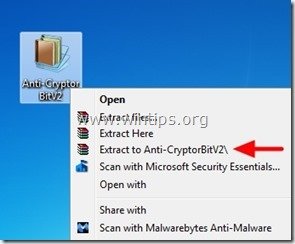
1. Download “Anti-CryptorBit” utility to your computer (e.g. your Desktop)
2. When download is completed, navigate to your Desktop and “Extract” the “Anti-CryptorBitV2.zip” file.
3. Now double-click to run the Anti-CryptorBitv2 utility.
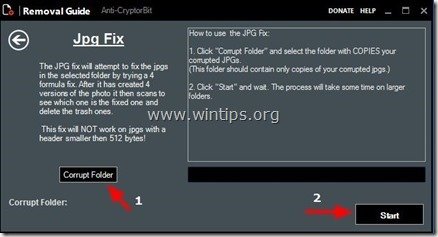
4. Choose what type of files you want to recover. (e.g. “JPG”)
5. Finally choose the folder that contains the corrupted/encrypted (JPG) files & then press the “Start” button to to fix them.
Cryptolocker – Virus Information & Decryption.
Cryptolocker (also known as “Troj/Ransom-ACP”, “Trojan.Ransomcrypt.F”) is a Ransomware nasty virus (TROJAN) and when it infects your computer, it encrypts all the files regardless of their extension (file type). The bad news with this virus is that, once it infects your computer, your critical files are encrypted with strong encryption and it is practically impossible to decrypt them. Once a computer is infected with Cryptolocker virus, then an information message appears on the victim’s computer demanding a payment (ransom) of 300$ (or more) in order to decrypt your files.
A detailed analysis of Cryptolocker ransomware infection and removal can be found in this post:
How to decrypt Cryptolocker infected files and get your files back:
In order to decrypt Cryptolocker infected files you have these options:
A. The first option is to pay the ransom. If you decide to do that, then proceed with the payment at your own risk because according to our research some users get their data back and some others don’t.
B. The second option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
C. If you don’t have a clean backup, then you can try to restore your files in previous versions from “Shadow Copies”. Observe that this procedure works only in Windows 8, Windows 7 and Vista OS and only if the “System Restore” feature was previous enabled on your computer and was not disabled after the Cryptolocker infection.
- Referral link: How to restore your files from Shadow Copies.
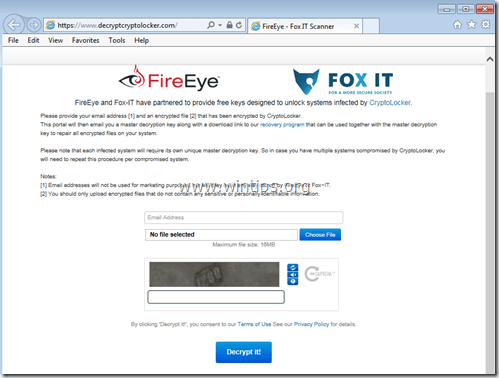
D. In August 2014, FireEye & Fox-IT have released a new service that retrieves the private decryption key for users that were infected by the CryptoLocker ransomware. The service is called 'DecryptCryptoLocker' (the service has discontinued), it is available globally and does not require users to register or provide contact information in order to use it.
In order to use this service you have to visit this site: (the service has discontinued) and upload one encrypted CryptoLocker file from the infected computer (Notice: upload a file that doesn’t contain sensitive and/or private information). After you do that, you have to specify an email address in order to receive your private key and a link to download the decryption tool. Finally run the downloaded CryptoLocker decryption tool (locally on your computer) and enter your private key to decrypt your CryptoLocker encrypted files.
More information about this service can be found here: FireEye and Fox-IT Announce New Service to Help CryptoLocker Victims.
CryptXXX V1, V2, V3 (Variants: .crypt , crypz, or 5 hexadecimal characters).
- CryptXXX V1 & CryptXXX V2 ransomware encrypts your files and adding the ".crypt" extension at the end of each file after infection.
- CryptXXX v3 adds the ".cryptz" extension after encryption of your files.
The trojan CryptXXX encrypts the following types of files:
.3DM, .3DS, .3G2, .3GP, .7Z, .ACCDB, .AES, .AI, .AIF, .APK, .APP, .ARC, .ASC, .ASF, .ASM, .ASP, .ASPX, ASX, .AVI, .BMP, .BRD, .BZ2, .C, .CER, .CFG, .CFM, .CGI, .CGM, .CLASS, .CMD, .CPP, .CRT, .CS, .CSR, .CSS, .CSV, .CUE, .DB, .DBF, .DCH, .DCU, .DDS, .DIF, .DIP, .DJV, .DJVU, .DOC, .DOCB, .DOCM, .DOCX, .DOT, .DOTM, .DOTX, .DTD, .DWG, .DXF, .EML, .EPS, .FDB, .FLA, .FLV, .FRM, .GADGET, .GBK, .GBR, .GED, .GIF, .GPG, .GPX, .GZ, .H, .H, .HTM, .HTML, .HWP, .IBD, .IBOOKS, .IFF, .INDD, .JAR, .JAVA, .JKS, .JPG, .JS, .JSP, .KEY, .KML, .KMZ, .LAY, .LAY6, .LDF, .LUA, .M, .M3U, .M4A, .M4V, .MAX, .MDB, .MDF, .MFD, .MID, .MKV, .MML, .MOV, .MP3, .MP4, .MPA, .MPG, .MS11, .MSI, .MYD, .MYI, .NEF, .NOTE, .OBJ, .ODB, .ODG, .ODP, .ODS, .ODT, .OTG, .OTP, .OTS, .OTT, .P12, .PAGES, .PAQ, .PAS, .PCT, .PDB, .PDF, .PEM, .PHP, .PIF, .PL, .PLUGIN, .PNG, .POT, .POTM, .POTX, .PPAM, .PPS, .PPSM, .PPSX, .PPT, .PPTM, .PPTX, .PRF, .PRIV, .PRIVAT, .PS, PSD, .PSPIMAGE, .PY, .QCOW2, .RA, .RAR, .RAW, .RM, .RSS, .RTF, .SCH, .SDF, .SH, .SITX, .SLDX, .SLK, .SLN, .SQL, .SQLITE, .SQLITE, .SRT, .STC, .STD, .STI, .STW, .SVG, .SWF, .SXC, .SXD, .SXI, .SXM, .SXW, .TAR, .TBK, .TEX, .TGA, .TGZ, .THM, .TIF, .TIFF, .TLB, .TMP, .TXT, .UOP, .UOT, .VB, .VBS, .VCF, .VCXPRO, .VDI, .VMDK, .VMX, .VOB, .WAV, .WKS, .WMA, .WMV, .WPD, .WPS, .WSF, .XCODEPROJ, .XHTML, .XLC, .XLM, .XLR, .XLS, .XLSB, .XLSM, .XLSX, .XLT, .XLTM, .XLTX, .XLW, .XML, .YUV,.ZIP, .ZIPX
How to decrypt CryptXXX files.
If you are infected with CryptXXX Version 1 or Version 2, then use Kaspersky's RannohDecryptor tool to decrypt your files.
If f you are infected with CryptXXX Version 3, then use Trend Micro's Ransomware File Decryptor. *
Note: Due to the advanced encryption of CryptXXX V3 virus, only partial data decryption is currently possible and you have to use a thrird party repair tool to repair your files like: http://www.stellarinfo.com/file-repair/file-repair-toolkit.php
Locky & AutoLocky (Variants: .locky)
Locky ransomware encrypts your files using RSA-2048 and AES-128 encryption and after the infection all your files are renamed with a unique – 32 characters- file name with the extension ".locky" (e.g. "1E776633B7E6DFE7ACD1B1A5E9577BCE.locky"). Locky virus can infect local or network drives and during infection creates a file named "_HELP_instructions.html" on every infected folder, with instructions on how you can pay the ransom and decrypt your files using the TOR browser.
AutoLocky is another variant of Locky virus. The main difference between Locky and Autolocky is that Autolocky will not change the original name of the file during infection. (e.g. If a file is named "Document1.doc" before infection, the Autolocky renames it to "Document1.doc.locky")
How to decrypt .LOCKY files:
- The first option is to clean the infected computer and then to restore your infected files from a clean backup (if you have one).
- The second option, if you don’t have a clean backup, is to restore your files in previous versions from “Shadow Copies”. How to restore your files from Shadow Copies.
- The 3rd option, is to use the Emsisoft's Decrypter for AutoLocky to decrypt your files. (The decrypter tool is working only for Autolocky).
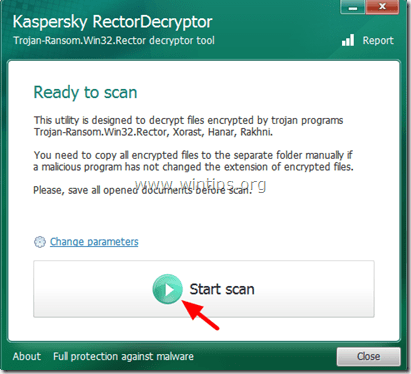
Trojan-Ransom.Win32.Rector – Virus Information & Decryption.
The Trojan Rector encrypts files with the following extensions: .doc, .jpg, .pdf .rar, and after the infection it makes them unusable. Once your files are infected with Trojan Rector, then the extensions of the infected files are changed to .VSCRYPT, .INFECTED, .KORREKTOR or .BLOC and this makes them unusable. When you try to open the infected files, then a message in Cyrillic characters is displayed on your screen which contains the ransom demand and the details for the payment. The cybercriminal who makes the Trojan Rector called “††KOPPEKTOP†† and asks to communicate with him via email or ICQ (EMAIL: v-martjanov@mail.ru / ICQ: 557973252 or 481095) to give instructions on how to unlock your files.
How to decrypt files infected with Trojan Rector and get your files back:
Advice: Copy all the infected files to a separate directory and close all open programs before proceeding to scan and decrypt the affected files.
1. Download Rector Decryptor utility (from Kaspersky Labs) to your computer.
2. When the download is completed, run RectorDecryptor.exe.
3. Press the “Start Scan” button to scan your drives for the encrypted files.
4. Let the RectorDecryptor utility to scan and decrypt the encrypted files (with extensions .vscrypt, .infected, .bloc, .korrektor) and then select the option to “Delete crypted files after decryption” if the decryption was successful. *
* After the decryption you can find a report log of the scanning/decryption process to the root of your C:\ drive (e.g. “C:\RectorDecryptor.2.3.7.0_10.02.2011_15.31.43_log.txt”).
5. Finally continue to check and clean your system from malware programs that may exist on it.
Source – Additional information: http://support.kaspersky.com/viruses/disinfection/4264#block2
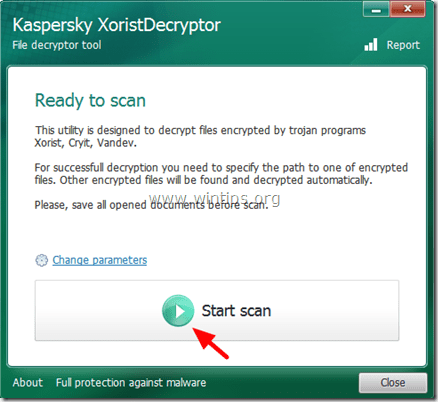
Trojan-Ransom. Win32.Xorist, Trojan-Ransom.MSIL.Vandev – Virus Information & Decryption.
The Trojan Ransom Xorist & Trojan Ransom Valdev, encrypts files with the following extensions:
doc, xls, docx, xlsx, db, mp3, waw, jpg, jpeg, txt, rtf, pdf, rar, zip, psd, msi, tif, wma, lnk, gif, bmp, ppt, pptx, docm, xlsm, pps, ppsx, ppd, tiff, eps, png, ace, djvu, xml, cdr, max, wmv, avi, wav, mp4, pdd, html, css, php, aac, ac3, amf, amr, mid, midi, mmf, mod, mp1, mpa, mpga, mpu, nrt, oga, ogg, pbf, ra, ram, raw, saf, val, wave, wow, wpk, 3g2, 3gp, 3gp2, 3mm, amx, avs, bik, bin, dir, divx, dvx, evo, flv, qtq, tch, rts, rum, rv, scn, srt, stx, svi, swf, trp, vdo, wm, wmd, wmmp, wmx, wvx, xvid, 3d, 3d4, 3df8, pbs, adi, ais, amu, arr, bmc, bmf, cag, cam, dng, ink, jif, jiff, jpc, jpf, jpw, mag, mic, mip, msp, nav, ncd, odc, odi, opf, qif, qtiq, srf, xwd, abw, act, adt, aim, ans, asc, ase, bdp, bdr, bib, boc, crd, diz, dot, dotm, dotx, dvi, dxe, mlx, err, euc, faq, fdr, fds, gthr, idx, kwd, lp2, ltr, man, mbox, msg, nfo, now, odm, oft, pwi, rng, rtx, run, ssa, text, unx, wbk, wsh, 7z, arc, ari, arj, car, cbr, cbz, gz, gzig, jgz, pak, pcv, puz, r00, r01, r02, r03, rev, sdn, sen, sfs, sfx, sh, shar, shr, sqx, tbz2, tg, tlz, vsi, wad, war, xpi, z02, z04, zap, zipx, zoo, ipa, isu, jar, js, udf, adr, ap, aro, asa, ascx, ashx, asmx, asp, aspx, asr, atom, bml, cer, cms, crt, dap, htm, moz, svr, url, wdgt, abk, bic, big, blp, bsp, cgf, chk, col, cty, dem, elf, ff, gam, grf, h3m, h4r, iwd, ldb, lgp, lvl, map, md3, mdl, mm6, mm7, mm8, nds, pbp, ppf, pwf, pxp, sad, sav, scm, scx, sdt, spr, sud, uax, umx, unr, uop, usa, usx, ut2, ut3, utc, utx, uvx, uxx, vmf, vtf, w3g, w3x, wtd, wtf, ccd, cd, cso, disk, dmg, dvd, fcd, flp, img, iso, isz, md0, md1, md2, mdf, mds, nrg, nri, vcd, vhd, snp, bkf, ade, adpb, dic, cch, ctt, dal, ddc, ddcx, dex, dif, dii, itdb, itl, kmz, lcd, lcf, mbx, mdn, odf, odp, ods, pab, pkb, pkh, pot, potx, pptm, psa, qdf, qel, rgn, rrt, rsw, rte, sdb, sdc, sds, sql, stt, t01, t03, t05, tcx, thmx, txd, txf, upoi, vmt, wks, wmdb, xl, xlc, xlr, xlsb, xltx, ltm, xlwx, mcd, cap, cc, cod, cp, cpp, cs, csi, dcp, dcu, dev, dob, dox, dpk, dpl, dpr, dsk, dsp, eql, ex, f90, fla, for, fpp, jav, java, lbi, owl, pl, plc, pli, pm, res, rnc, rsrc, so, swd, tpu, tpx, tu, tur, vc, yab, 8ba, 8bc, 8be, 8bf, 8bi8, bi8, 8bl, 8bs, 8bx, 8by, 8li, aip, amxx, ape, api, mxp, oxt, qpx, qtr, xla, xlam, xll, xlv, xpt, cfg, cwf, dbb, slt, bp2, bp3, bpl, clr, dbx, jc, potm, ppsm, prc, prt, shw, std, ver, wpl, xlm, yps, md3.
After the infection, Trojan Ransom Xorist compromises your computer's security, makes your computer unstable and displays messages on your screen demanding a ransom in order to decrypt the infected files. The messages contain also information on how to pay the ransom in order to get the decryption utility from the cybercriminals.
How to decrypt files infected with Trojan Win32.Xorist or Trojan MSIL.Vandev:
Advice: Copy all the infected files to a separate directory and close all open programs before proceeding to scan and decrypt the affected files.
1. Download Xorist Decryptor utility (from Kaspersky Labs) to your computer.
2. When the download is completed, run XoristDecryptor.exe.
Note: If you want to delete the encrypted files when the decryption is completed, then click the “Change parameters” option and check the “Delete crypted files after decryption” check box under “Additional Options”.
3. Press the “Start Scan” button.
4. Enter the path of at least one encrypted file and then wait until the utility decrypts the encrypted files.
5. If the decryption was successful, reboot your computer and then scan and clean your system from malware programs that may exist on it.
Source – Additional information: http://support.kaspersky.com/viruses/disinfection/2911#block2
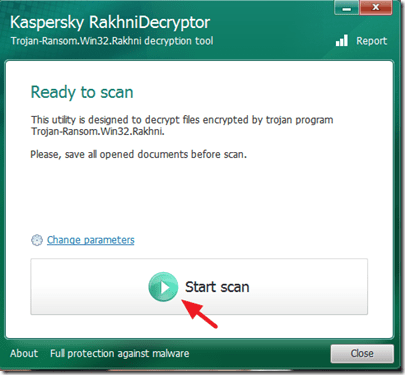
Trojan-Ransom.Win32.Rakhni – Virus Information & Decryption.
The Trojan Ransom Rakhni encrypts files by changing files extensions as follows:
<filename>.<original_extension>.<locked>
<filename>.<original_extension>.<kraken>
<filename>.<original_extension>.<darkness>
<filename>.<original_extension>.<nochance>
<filename>.<original_extension>.<oshit>
<filename>.<original_extension>.<oplata@qq_com>
<filename>.<original_extension>.<relock@qq_com>
<filename>.<original_extension>.<crypto>
<filename>.<original_extension>.<helpdecrypt@ukr.net>
<filename>.<original_extension>.pizda@qq_com
After the encryption, your files are unusable and your system security is compromised. Also the Trojan-Ransom.Win32.Rakhni creates a file on your %APPDATA% folder named “exit.hhr.oshit” that contains the encrypted password for the infected files.
Warning: The Trojan-Ransom.Win32.Rakhni creates the “exit.hhr.oshit” file that contains an encrypted password to the user's files. If this file remains on the computer, it will make decryption with the RakhniDecryptor utility faster. If the file has been removed, it can be recovered with file recovery utilities. After the file is recovered, put it into %APPDATA% and run the scan with the utility once again.
%APPDATA% folder location:
- Windows XP: C:\Documents and Settings\<username>\Application Data
- Windows 7/8: C:\Users\<username>\AppData\Roaming
How to decrypt files infected with Trojan Rakhni and get your files back:
1. Download Rakhni Decryptor utility (from Kaspersky Labs) to your computer.
2. When the download is completed, run RakhniDecryptor.exe.
Note: If you want to delete the encrypted files when the decryption is completed, then click the “Change parameters” option and check the “Delete crypted files after decryption” check box under “Additional Options”.
3. Press the “Start Scan” button to scan your drives for encrypted files.
4. Enter the path of at least one encrypted file (e.g. “file.doc.locked”) and then wait until the utility recovers the password from the “exit.hhr.oshit” file (mind the Warning) and decrypts your files.
Source – Additional information: http://support.kaspersky.com/viruses/disinfection/10556#block2
Trojan-Ransom.Win32.Rannoh (Trojan-Ransom.Win32.Cryakl) – Virus Information & Decryption.
The Trojan Rannoh or Trojan Cryakl encrypts all files on your computer in the following way:
- In case of a Trojan-Ransom.Win32.Rannoh infection, file names and extensions will be changed according to the template locked-<original name>.<four random letters>.
- In case of a Trojan-Ransom.Win32.Cryakl infection, the tag {CRYPTENDBLACKDC} is added to the end of file names.
How to decrypt files infected with Trojan Rannoh or Trojan Cryakl and get your files back:
Important: The Rannoh Decryptor utility decrypts files by comparing one encrypted and one decrypted file. So if you want to use the Rannoh Decryptor utility to decrypt files you must own an original copy of at least one encrypted file before the infection (e.g. from a clean backup).
1. Download Rannoh Decryptor utility to your computer.
2. When the download is completed, run RannohDecryptor.exe
Note: If you want to delete the encrypted files once the decryption is completed, then click the “Change parameters” option and check the “Delete crypted files after decryption” check box under “Additional Options”.
3. Press the “Start Scan” button.
4. Read the “Information required” message and then click “Continue” and specify the path to an original copy of at least one encrypted file before the infection (clean – original – file) and the path to the encrypted file (infected – encrypted -file).
5. After the decryption, you can find a report log of the scanning/decryption process to the root of your C:\ drive. (e.g. “C:\RannohDecryptor.1.1.0.0_02.05.2012_15.31.43_log.txt”).
Source – Additional information: http://support.kaspersky.com/viruses/disinfection/8547#block1
TeslaCrypt (Variants: .ecc, .ezz, .exx, .xyz, .zzz,. aaa, .abc, .ccc, & .vvv)
The TeslaCrypt ransomware virus adds the following extensions to your files: .ecc, .ezz, .exx, .xyz, .zzz,. aaa, .abc, .ccc, & .vvv.
How to decrypt TeslaCrypt files:
If you are infected with TeslaCrypt virus then use one of these tools to decrypt your files:
- TeslaDecoder: More information and instructions about using TeslaDecoder can be found in this article: http://www.bleepingcomputer.com/forums/t/576600/tesladecoder-released-to-decrypt-exx-ezz-ecc-files-encrypted-by-teslacrypt/
- Trend Micro Ransomware File Decryptor.
TeslaCrypt V3.0 (Variants: .xxx, .ttt, .micro, .mp3)
The TeslaCrypt 3.0 ransomware virus adds the following extensions to your files: .xxx, .ttt, .micro & .mp3
How to decrypt TeslaCrypt V3.0 files:
If you 're infected with TeslaCrypt 3.0 then attempt to recover your files with:
- Trend's Micro Ransomware File Decryptor tool.
- RakhniDecryptor (How to Guide)
- Tesla Decoder (How to Guide)
- Tesladecrypt – McAfee
TeslaCrypt V4.0 (File name and extension are unchanged)
To decrypt TeslaCrypt V4 files, try one of the following utilities:
- Trend's Micro Ransomware File Decryptor tool.
- RakhniDecryptor (How to Guide)
- Tesla Decoder (How to Guide)
We're hiring
We're looking for part-time or full-time technical writers to join our team! It's about a remote position that qualified tech writers from anywhere in the world can apply. Click here for more details.
- How to Disable or Remove BitLocker from Windows RE. - April 24, 2024
- FIX: Error 0x8007025d in Windows 10 Update. - April 22, 2024
- How to Disable Device Encryption in Windows 11/10. - April 17, 2024






July 25, 2019 @ 6:30 pm
how can i decript novasof ransomware virus from my .dwg file
July 26, 2019 @ 12:45 pm
@Prabhat: Read the instructions at this link: https://www.bleepingcomputer.com/forums/t/671473/stop-ransomware-stop-puma-djvu-promo-drume-help-support-topic/
April 12, 2019 @ 8:09 am
Hi all my photos are affected by a virus and I am not able to open them, it's very important pics.
The file extension is like .JPG.taywuwpofp.
Can somebody help me in recovery of my pics plz
September 10, 2017 @ 10:26 am
Hello!
One can tell someone to decrypt the encrypted file which has been renamed as follows:
.
For example.:
I've tried "Rannoh decryptor" but I did not succeed, the error message was:
17: 44: 05.0961 0x158c Can not initialize on pair
17: 44: 05.0961 0x158c Can not init decryptor
September 11, 2017 @ 11:28 am
@RendszergazdaNyh: Go to ID Ransomware and upload the Ransom Note and a Sample of an Encrypted file, to identify the ransomware name/variant and -if exists- a decrypter tool.
September 12, 2017 @ 2:18 pm
Hello!
I tried but did not recognize it.
The homepage message .: "Unable to determine ransomware".
Otherwise my first message was missing the file pattern…
Filename: 5-10 random characters
Extension: 2-5 random characters
The example.:
0y36a.t4
82bboay8.s6
9pqa0gvbh9.n60
aj5y4.lx4v5
1nd5nd8o7.ogdq9
Is not this so familiar to someone?
July 16, 2017 @ 7:44 pm
Hi to all,
yesterday my files encrypted by ransom and files extension changed to ".goro" with a html file name which its name is : "how_to_back_files.HTML" and email address is "mk.goro@aol.com" is it any decryption tool for this ransom-ware ?
Thanks.
April 18, 2017 @ 12:30 am
Hello All,
My system have been also attack and extension of all files and system files are now .AES_NI_0DAY
Please what is the good tool to restore my file. I don't have a backup.
thanks
April 18, 2017 @ 5:18 pm
@Blaise: Unfortunately there is not exist a free decryptor tool for this type of ransomware.
February 3, 2017 @ 11:20 pm
Is there some solution already for Cryptowall 3 decoding?
February 4, 2017 @ 10:26 am
@rina: Unfortunately -until today- is not possible to decrypt Cryptowall encrypted files.
January 9, 2017 @ 1:49 am
hello … I've just received a ransomware virus badnews … I want data back … can anyone please give my solution because data is very important. I received this virus when sending e-mail documents. My document change to how to encrypted file .hta
January 4, 2017 @ 11:26 am
Ciao nel mio pc son stati crittografati i file con estensione .a998, è gia in giro qualche tool decrypter ? Grazie
January 5, 2017 @ 10:11 am
@Luca: Unfortunately I don't know this type of ransomware. Go to ID Ransomware and upload the Ransom Note and a Sample of an Encrypted file, to identify the ransomware name/variant.
December 25, 2016 @ 4:56 pm
Thank you!!! the tools mentioned here saved my a*s.
December 16, 2016 @ 6:32 pm
Oh my God … so there's nothing to do. T_T
December 15, 2016 @ 7:49 pm
Hi, thank you for replying. I used ID Ransomware and appreciated the following message:This ransomware has no known way of decrypting data at this time.
It is recommended to backup your encrypted files, and hope for a solution in the future.
I really don't know what to do now.
December 16, 2016 @ 6:30 pm
@Ariane: If you don't have clean backups, then hope for a solution in the future.
December 14, 2016 @ 2:50 pm
Hi, All my excel, word, JPEg files have automatically added with .crypted in the network places while in the Desktop, Documents where files are perfectly okay. i could not able to view the files now. Can you please suggest me to restore all my files.
December 15, 2016 @ 1:16 pm
@Yaser: The encrypted files are located on another computer on your network, not in yours. Find and disconnect the infected computer (with the encrypted shared files) from the network. Then try to decrypt the encrypted files with the Trend Micro Ransomware File Decryptor tool. (run the tool on the infected computer)
December 14, 2016 @ 10:45 am
Please, I need a lot of help, my files are with the extension: A56C and I don't know which virus this is and how to remove it.
December 14, 2016 @ 2:44 pm
@Ariane: Go to ID Ransomware and upload the Ransom Note and a Sample of an Encrypted file, to identify the ransomware name/variant.
November 14, 2016 @ 5:37 pm
This is the message in the .TXT file
===============================================================================
!!! we coderen uw bestanden met Crypt0L0cker virus !!!
===============================================================================
Uw belangrijke bestanden (inclusief die op het netwerk schijven, USB, etc):
foto's, video's, documenten, enz. werden gecodeerd met onze Crypt0L0cker virus.
De enige manier om uw bestanden te herstellen is om ons te betalen. Anders zal
uw bestanden verloren gaan.
Om uw bestanden te herstellen moet u betalen..
Om uw bestanden te herstellen opent u onze website
htttp://anbqjdoyw6wkmpeu.tormidle.at/ce7fase.php?user_code=eezdar&user_pass=1029
en volg de instructies.
Als de website niet beschikbaar is kunt u als volgt te werk:
1. Download en installeer TOR-browser: htttps://www.torproject.org/download/download-easy.html.en
2. Na de installatie voert u de browser en voer het adres: htttp://anbqjdoyw6wkmpeu.onion/ce7fase.php?user_code=eezdar&user_pass=1029
3. Volg de instructies op de website.
===============================================================================
November 14, 2016 @ 3:26 pm
Hello, in september my computer is infected by a virus, but i don't know what kind. a lot of files has been renamed like .enc and encrypted. and every folder has 2 files "HOW_TO_RESTORE_FILES.HTML" and HOW_TO_RESTORE_FILES.TXT". I tried several decryption tools but with no succes. Who can help me?
November 14, 2016 @ 3:30 pm
I found a possible name for the virus: Cryptohasyou.
November 14, 2016 @ 3:57 pm
@Herman: Probably your 're infected by Crypt0l0cker or TorrentLocker and unfortunately until today there is no way to recover your files for free.
November 14, 2016 @ 4:26 pm
Thank you. Do you think that a decrypt tool will be come available?
November 15, 2016 @ 11:35 am
@Herman: I don't know if a decryptor tool become available. If you want to find out the exact name of virus navigate to ID Ransomware website and upload a sample of an encrypted file and the ransom note.
November 14, 2016 @ 4:28 pm
And how can i check if it is the Crypt0l0cker or the Torrentlocker?
November 13, 2016 @ 2:19 pm
my doc, pdf and jpeg files are corrupt and they dont open. the file type is changed to
(.0117F51D_luck) extension.
how to repair these files and i dont have backup nor i can restore system because no secure point is there to restore.
please help me!!
November 14, 2016 @ 9:49 am
@kushagra rai: Unfortunately there is not exist a free decryptor tool for this type of ransomware.
November 11, 2016 @ 3:58 am
Just got a CERBER4 ransom virus myself.. All files end with .b7a7 and couldn't find a solution yet :\
November 11, 2016 @ 9:53 am
@Gaarzen: Unfortunately there is not exist a free decryptor tool for CERBER 4.0 until today.
October 26, 2016 @ 10:51 pm
My doc , picture files , pdf and ppt files have all been encrypted by cerber ransomware and the extension has been changed to .a83c. Is there a tool to decrypt these?
October 27, 2016 @ 1:23 pm
@ferydon babaei: Please nagivate to this website https://id-ransomware.malwarehunterteam.com/ and identify which version of cerber ransomware is.
October 24, 2016 @ 11:56 am
My files encrypted by cerver4. All files converted in . exaple 07wOqQurs5.83e5
October 24, 2016 @ 1:13 pm
@Punit Gattani: As I know there is not a free decryptor tool for cerber4 encrypted files.
October 25, 2016 @ 11:39 am
Should we expect solution for this in near future . So that i keep backup of all files.
October 21, 2016 @ 8:51 pm
Hello! My computer is infected with .crypted ransomware. I’ve used these methods:
– ShadowExplorer ( http://www.shadowexplorer.com/downloads.html )
– Manual guide ( http://manual-removal.com/crypted/ )
– TrendMicro tool (https://success.trendmicro.com/solution/1114221)
But nothing works for me. Is there a chance to decrypt my files?
October 22, 2016 @ 11:08 am
@Alen: As I know these viruses adds the .crypted extention: Nemucod & Xorist. Try one of the following keys.
1. https://decrypter.emsisoft.com/nemucod
2. https://decrypter.emsisoft.com/xorist
October 20, 2016 @ 9:00 am
8150811044…this is my whats app no….. if u saw my msg ……so reply in whats app and suggest me something to slove my problem……
October 20, 2016 @ 8:48 am
Actually i downloaded shadedecrpter and rannohdecryter and rakhnidecrpter…but its not scanning….its shows waring like specify the original copy of the specified file is required for successful decryption…
October 20, 2016 @ 8:34 am
my files names like ADeRa6yXxd and ceber ramsomware..
October 20, 2016 @ 8:53 am
@pratibha bhogun: For Cerber use this tool: https://success.trendmicro.com/solution/1114221
October 20, 2016 @ 8:32 am
my files names like ADeRa6yXxd
October 13, 2016 @ 7:00 am
All of my files got infected with cerber ransomware with .bebc extension for which I am not able to find a decryptor tool. Can anybody help me to decrypt the files as I have some important data encrypted and I dont have any backup at all.
October 13, 2016 @ 5:11 pm
@Jiten: Unfortunately I don't know this ransomware.
October 14, 2016 @ 4:13 am
for me. you have?
October 14, 2016 @ 4:55 pm
@ardiles: Unfortunately no :(
October 13, 2016 @ 6:38 am
hello,
all my files were encrypted with file type as '.a294'. Any suggestions to convert.
October 12, 2016 @ 9:31 am
Hi,
My whole documents and photos have been encrypted by CERBER RANSOMWARE. How can I retrieve all my documents and photos as I dont have any kind of backup at all.
October 12, 2016 @ 12:49 pm
@Raihan: Use Trend Micro Ransomware File Decryptor.
October 8, 2016 @ 8:01 am
Ciao a tutti. Molto interessante quanto letto. Qualcuno di voi sa come decriptare i file locked?
Mi sono stati criptati nel 2012.
Magari ora c'è la possibilità di decriptare.
Grazie a tutti.
October 1, 2016 @ 5:07 pm
hi,
all my files were encrypted with file type as '.encrypted'. Any suggestions to convert.
October 2, 2016 @ 9:39 am
@shiva: Hello, the filenames are changed or not? Tell me the Ransom notes filenames.
You can try with Rakhni Decryptor tool
September 28, 2016 @ 4:22 pm
Which antivirus is best to remove the ransomeware virus ?
September 29, 2016 @ 9:23 am
@Mobin: Follow this guide to clean the ransomware and run Eset Online Scanner at the end.
September 18, 2016 @ 10:21 am
Dir Sir,
My computer has been infected with .ceber3 extension encrypted all jpg file extension change, how to decrypt.ceber3
September 19, 2016 @ 9:42 am
@Satish: Unfortunately at this time there is no decryption tool for .ceber3
August 20, 2016 @ 5:37 pm
Hi,
My computer has been infected with Cryptowall virus since 12/1/15. Fortunately, the virus has been removed, however, I would like to know if you know of anything that could possibly decrypt the files that have been infected by Cryptowall virus? If so, I am in desparate need of your assistance. Thank you in advance for any assistance you are able to provide me at this critical time.
Respectfully,
Charolette Alexander
August 22, 2016 @ 11:36 am
@Charolette Alexander: Unfortunately at this time there is no a way to decrypt Crypotowall files.
August 18, 2016 @ 4:13 pm
Hi,
Unfortunately opened an invoice from what i thought was a client changed all my dwg files and jpg to .mp3 files.
How do I find out which of the above decryptors to use?
August 19, 2016 @ 10:19 am
To decrypt your files use either the Trend Micro Ransomware File Decryptor or the TeslaDecoder
Good luck!
August 13, 2016 @ 9:47 am
cerber decrypt with trend micro it is working
August 3, 2016 @ 9:30 pm
There is no solution yet. I recommend not to pay. After you pay to "space_rangers-at-aol.com the stop answer back. They block your email address. Sorry. Always Backup your files.
July 23, 2016 @ 1:10 pm
my shared folders files are encrypted data Vegclass@aol.com.xtbl .how it can dycrypt?
July 25, 2016 @ 9:19 am
@atif: I don't know a decryptor tool for this ransomware. Try to restore your files with Shadow Explorer. Also scan your network (computers) to find the infection source.
July 22, 2016 @ 1:30 pm
sir
Please let me know cerber ransomware decrypt tool immediately
July 22, 2016 @ 4:58 pm
@jagan: Use this tool: http://esupport.trendmicro.com/solution/en-US/1114221.aspx
Good luck!
July 17, 2016 @ 10:47 am
@Lakonst,
Hi Dear Yetserday only my all files got encrypted with .xtbl extension is there any way yet to decrypt this data??
July 19, 2016 @ 9:43 am
@AJIT: Unfortunately I don't know if there is exist a decrypter tool for this type of ransomware. Try to restore your files in previous version by using Shadow explorer.
June 28, 2016 @ 5:11 am
Hello, I still need help. I am grateful for all the information that has been on here. My laptop was encrypted by CryptXXX (not sure what version.) Thank fully most Microsoft files and adobe are being decrypted using the Trend Micro link, but I am having no luck with any .jpg…. it shows a new file with the original name but it cannot be opened. Has anyone had any luck with anything working on .jpg??? I am desperate; I could not pay the ransom (not that I would have paid it) but one site said once they delete their key all hope is lost…. please, if anyone can help!
July 11, 2016 @ 3:37 pm
you can try [rannohdecryptor.exe], little tool of Kaspersky. version 1.9.1.1.
It decrypted most of my infected documents.
Only a few cannot be decrypted. I don't know why.
June 26, 2016 @ 11:14 pm
Hello Lakinst, thank you for the good post. I was infected with a virus and locked all my files, I paid the ransom, the hacker send me a dec.exe file, all what I need to do is to drag my file to the .exe and it decrypt them. This method worked for the smaller file. I have a large file over 4 GB ( database) that does not work. I'm able to extract the hacker .exe it contains 3 small files ( .data, .rdata and a small text file) do you know if any software that I can use along with the hacker file to decrypt the file? Thank you
June 27, 2016 @ 10:44 am
@Dave Toss: I don;t know any software to decrypt the file.
June 27, 2016 @ 6:34 pm
Thank you.
June 25, 2016 @ 12:57 am
hi all,
my laptop infected by .crypz any support please ?
June 25, 2016 @ 7:17 am
@ahmed: Try to decrypt files with Trend Micro’s Ransomware File Decrypter tool.
June 23, 2016 @ 5:10 am
I got mine encrypted, at the end of each file name is .crypted
June 24, 2016 @ 4:30 am
Try to do the advise of @lakonst up there. It works for me.
June 22, 2016 @ 3:27 pm
Excellent article – recovered *.crypz ransomware files using Win 7 file restore as explained.
A simple solution often overlooked.
June 15, 2016 @ 11:32 am
I have all my personal files encrypted a month ago. Today, with the tool [RansomwareFileDecryptor] many of them are decrypted. Thank to your efforts.
And I think the malware is cryptXXX V2.
However, some video files encrypted with the name "[original name].MOV.crypt" and "[original name].AVI.crypt" can not be decrypted. What should I do?
June 4, 2016 @ 9:23 am
We have the .crypt virus also but cannot figure out which decryptor will work. Or rather whatever we tried does not work. Can anyone help us please how to get our files back. We did not have recovery or versions or shadow copy on. Thanks in advance for your help. Please we are desperate.
May 31, 2016 @ 1:04 pm
Hi there,
Thanks for sharing great information.
I've been infected with Trojan Cryakl some weeks ago.
I used "rannohdecryptor.exe" released by Kaspersky and recovered most of my files but it cannot recover xml, flv mkv, mp4, html and csv files.
Do you have any idea to recover them?
Thanks for your attention.
Ferin.
June 25, 2016 @ 11:01 pm
Hey, glad everyone is willing to share information about this!!
I tried using "rannohdecryptor" but it did not work for me at all. I did successfully use the following link for music & Microsoft files: http://esupport.trendmicro.com/solution/en-US/1114221.aspx Still a work in progress, however does not work on jpg files, so if anyone has any ideas please, please help! Thanks & good luck!!
May 27, 2016 @ 12:03 pm
Hi Ryza use EaseUS data recovery , it will work. im also from the philippines
May 26, 2016 @ 10:16 am
Hello I came from the philippines ! I also facing that problem right now all my files extension is .crypt, My computer(Window 7) is recently infected . Last May 24,2016
The problem is i dont have a clean back up and even shadow copy can't bring my original files back i also try spyhunter, teslacrypt etc.
Please advice for possible solution . Thank you
May 28, 2016 @ 3:41 am
Hi Ryza, I'm from the philppines too. I got the virus on the same day you got it. still looking for a way to decrypt the files. Have you fixed yours already?
June 23, 2016 @ 8:00 am
Raine Kindly Do the advice of lakonst . Im currently doing it. I hope all my files or not even all atleast 80% be recovered.
June 9, 2016 @ 7:55 am
Hi Ryza, did u find any solution?
June 9, 2016 @ 9:40 am
@khris: Try to decrypt files by using Using the Trend Micro Ransomware File Decryptor
June 21, 2016 @ 6:06 am
We successfully decrypt file but when we try to open it its corrupted :(
June 21, 2016 @ 9:29 am
@Ryza: Due to the advanced encryption of this particular Crypto-Ransomware, only partial data decryption is currently possible on files affected by CryptXXX V3, and you have to use a thrird party repair tool to repair your files like: http://www.stellarinfo.com/file-repair/file-repair-toolkit.php
June 21, 2016 @ 9:35 am
Thank you for the information. I will also try this one .
June 23, 2016 @ 8:02 am
Thank you for the information @lakonst :)
I try to recover some of my files and viola ! it works . Im waiting for my other files to be recovered . Thank you so much for the information
May 11, 2016 @ 2:58 pm
Dear ,
Thank you for sharing such information. Few days back my files are encrypted by "LMUWMG" viruses. All files are not change and not opening. Please share the best solution how i can get my files back. Please also reply me on (hassan.ahmed45@gmail.com).
Regards,
Hassan
April 27, 2016 @ 7:33 am
Hi,
i have used the Rannoh Decryptor, this work fine, only files larger 150MB can the program not decrypt. Im happy. My Comp. was with RSA-4096 infected.
See:
" NOT YOUR LANGUAGE? USE https://translate.google.com
What happened to your files ?
All of your files were protected by a strong encryption with RSA4096…"
April 8, 2016 @ 4:12 am
Hi, Thank you very much for helping people to find a way to solve this things. In my case, a computer was infected (exactly march 18th) with a virus that encrypted all the files without changing their original names. And created in all the infected folders, three files named RECOVER .png .HTML and .txt Is there a way to decrypt the files? Thank you very much
April 8, 2016 @ 9:36 am
@Markus: 1. Try to restore your files from Shadow Copies. 2. Try to recover your files by using Easeus Data Recovery.
Good luck!
March 26, 2016 @ 8:59 am
Sir,
I have .jpeg file taken form camera which was converted by virus with format like (v5saui7w.f0o30). Please suggest how to recover or decrypt this jpeg files
March 26, 2016 @ 2:47 pm
hi there. Unfortunately, The only method to get your files back is from a clean backup.
March 26, 2016 @ 3:27 am
Hello all the files well most of the files have had the extension changed to .lol and I have a text file named how to get data.txt the file starts off "Hello boys and Girls" any hope of getting these decrypted.
March 26, 2016 @ 2:47 pm
hi there. Unfortunately, The only method to get your files back is from a clean backup.
March 25, 2016 @ 1:51 pm
Hi Lakonst;
Thanks for all your efforts in guiding the Virus infectors!!!
My Case is a pretty different one. I also got infected by the Crypto Virus.But I don't have any backup/restore points.I had formatted my Laptop and copied the files.But I am still unable to open the files. The Message I get is : "Windows Photo Viewer can't open this picture because either Photo Viewer doesn't support this file format,or you don't have latest updates to Photo Viewer". Can you guide me in getting my files back !!
March 26, 2016 @ 2:46 pm
hi there. Unfortunately, The only method to get your files back is from a clean backup.
March 21, 2016 @ 11:06 am
Hello,
My Windows 7 was infected with a ransom virus. It has encrypted all my files in all the directories and the following 2 files are added to all the directories :HELP_DECRYPT.TXT, HELP_DECRYPT.PNGI have tried most of the file recovery softwares mentioned online, please advice on how to recover my files.
Thanks !
March 21, 2016 @ 5:16 pm
@Raluca: Your files are infected with Cryptowall v3.0 virus. Unfortunately at this time there is no decryption tool for CryptoWall files. Do you have a clean backup of your files to another media? If so, then clean your computer and then restore your files from the backup. If you haven’t a clean backup then try to restore your files from Shadow Copies (if the virus has not delete them yet). The last choice is to pay the ransom to get your files back, but it is risky because criminals are not trusted persons.
March 15, 2016 @ 10:14 pm
Hi, i have got some very important video files in .mxf format, but have gotten encrypted and become .mxf.xml
Im not sure what to do now,
It is important to decrypt them, I need help and suggestion.
March 16, 2016 @ 12:27 pm
@ Priyanka Daga: Unfortunately I don't know how this virus acts. Do you have a clean backup of your files to another media? If so, then clean your computer first (by using this guide) and then restore your files from the backup. If you haven't a clean backup then use this guide to restore your files from Shadow Copies (if the virus has not delete them yet). The last choice is to pay the ransom to get your files back, but it is risky because criminals are not trusted persons.
March 10, 2016 @ 8:42 am
Hi, I really hope you can help me. My laptop got infected as all document files extension turned into mp3. I have very important excel sheets. I don't have the previous version thing so please tell me if there is any other solution ??? Thanks
March 10, 2016 @ 6:09 pm
@Jia: Your files got encrypted by TeslaCrypt 3.0 ransomware. Unfortunately there is not a way yet to decrypt your files
February 28, 2016 @ 10:39 pm
Thanks a lot.
February 2, 2016 @ 10:42 pm
My computer was infected with virus in last month. I scanned whole computer with kaspersky antivirus I get nothing after that. After researching I found out that virus was self destructive and it eliminates itself after creating a damage to files. Most of the files are encrypted with virus and I am facing hard time to decrypt it back. All the files are encrypted with .LOL extension and I couldn’t find any legitimate software to decrypt that. Do you have any suggestion on this?
March 11, 2016 @ 10:36 am
@Vaibhav Kalve: Use "Tesla Decoder" to decrypt your files. Read the instructions here: http://www.bleepingcomputer.com/forums/t/576600/tesladecoder-released-to-decrypt-exx-ezz-ecc-files-encrypted-by-teslacrypt/
October 22, 2015 @ 5:38 pm
Hi,
My Windows 7 dell inspiron is infected with a ransom virus. It has encrypted all my files in all the directories and the following 2 files are added to all the directories :
HELP_DECRYPT.TXT, HELP_DECRYPT.PNG
I have tried most of the file recovery softwares mentioned online, please advice if anybody knows how to decrypt my files and remove the this particular virus.
Thanks !
Iti
October 4, 2015 @ 1:03 pm
Job done, I would like to thank you very much
August 11, 2015 @ 12:19 am
Hi
My doc and picture files have all been encryped and the extension has been changed to .jpg.ezz Is there a tool to un decrypt these?
Thx
August 15, 2015 @ 11:37 am
@Alan: Try to decrypt your files by using TeslaDecoder or Cisco's TeslaDecrypt.
June 30, 2015 @ 9:58 am
HI,
I have this crypto locker on my computer but i dont have the previous restore as I dont have the restore point. Do you know, how to get the files back as I already removed the virus from he computer. This kasper thing is of no help
June 30, 2015 @ 5:12 pm
@Andy Watson: :( The only way to restore files from cryptolocker, is by using a previous restore point.
June 26, 2015 @ 1:50 pm
Hi! Do you know which virus encrypt with extension {name of file}.{extension}id-{10 random numbers}_request@inbox.com? And it is possible to decrypt this files?
Thank you
June 26, 2015 @ 4:58 pm
@Izabella: Hi, I don't know about this virus.
October 19, 2015 @ 2:35 pm
Hi Izabella,
have you found a solution to your problem?
April 29, 2015 @ 11:01 pm
Hello, I could clean my computer from CryptoLock using Norton Power Eraser (NPE), perfect.
The thing is that I've tried to send an encripted file to ht**tps://www.decryptcryptolocker.com/ and they answer "Invalid File: The file does not seem to be infected by CryptoLocker. Please submit a CryptoLocker infected file.
The virus was Cryptolocker, sure…and all the infected files has now this form:
..
Could you help me, please?
Best regards,
Ignasi
April 30, 2015 @ 7:30 am
@Ignasi: There are many versions of Cryptolocker virus. Have you try to restore your files in previous version?
April 15, 2015 @ 1:15 pm
no hope for this. just format and accept reality lol
March 14, 2015 @ 8:35 am
This is the new generation of malware bill gates predicted. I have seen people pay ransom of 30$ only and receiving the unlocks,I believe one of these ransomware is 2048bit enc,so it's scary it's ruthless,but above all this,is bitcoin problem to,I mean they should be having accounts,wallets,disabled. It's sad the bitcoin community must now wear.
I hope that you can get stabler removal apps,because clearly,some of them are not working.
Goodluck troops.
Xd
February 22, 2015 @ 11:54 pm
Hello. I stupidly opened a zip file a month ago. i thought it was from a collegue. it was not and subsequently all my files (.doc .xls .jpeg .pdf) now have the following extention added after the usual file extention .tksxdzj. I did not receive any ransom request. However all my programs still work (office etc).
Our IT guy removed the virus but the files are now unuseable. at the time i was running AVG (purchased, not free). I know it was my own fault, but can you help? Any suggestions welcome.
kind regards
mauritz
February 23, 2015 @ 2:10 pm
Try to restore your files to a previous version.
November 18, 2014 @ 6:54 pm
I installed one of the decrypter files you provided and it deleted the jpeg file!
November 19, 2014 @ 12:21 pm
The decrypter utilities are not provided from me and they are only recommended (here) for the specific problems.