Remove Ice Virus permanently (Removal Instructions)
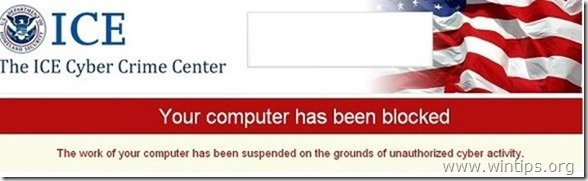
The "Ice Cyber Crime Center" ransom-ware virus locks your computer and asks for a fee to unblock it. Specifically when this virus infects your computer, you receive a message on your screen that informs you that ICE CYBER CRIME CENTER has blocked your computer because you accessed illegal or pornographic material.
The ICE CYBER CRIME CENTER virus also makes it impossible to use your computer, unless you pay a penalty of 300$ (or more) using MoneyPack transfer services because illegal activity was detected on your computer. As with other versions of ransomware viruses, the fake warning message seems real because it displays your location, your IP address and your own photo (or video) captured by your webcam.
Notice that the fake warning message that comes with this virus, is not associated with the government or any police, justice or legal department.
If you want to clean your computer from the Ice Cyber Crime virus, follow the steps below:
ICE CYBER CRIME CENTER Fake Warning message:
“The ICE Cyber Crimes Center
The Common Law in the will of Mankind Issuing from the Life of the People
YOUR COMPUTER HAS BEEN BLOCKED!
The work of your computer has been suspended on the grounds of unauthorized cyber activity.Possible violations are described below:
Article -174. Copyright
Imprisonment for the term of up to 2-5 years
(The use or sharing of copyrighted files). A fine from 18,000 up to 23,000 USDArticle – 183. Pornography
Imprisonment for the term of up to 2-3 years
(The use of distribution of pornographic files). A fine from 18,000 up to 25,000 USDArticle – 184. Pornography involving children (under 18 years)
Imprisonment for the term of up to 10-15 years
(The use or distribution of pornographic files). A fine from 20,000 up to 40,000 USDArticle – 104. Promoting Terrorism
Imprisonment for the term of up to 25 years without appeal
(Visiting the websites of terrorist groups). A fine from 35,000 up to 45,000 USDArticle – 68. The distribution of virus programs
Imprisonment for the term of up to 2 years
(The development or distribution of virus programs, which have caused harm to other computers). A fine from 15,000 to 28,000 USDHow do I unlock computer using MoneyPak?
1. Find a retail location near you.
2. Look for a MoneyPak in the prepaid section. Take it to the cashier and load it with cash. A service fee of up to $4.95 will apply.
3. To pay fine, you should enter the digits MoneyPak resulting code in the payment form and press Pay MoneyPak.
In connection with the decision of the Government as of January 26, 2013, all of the violations described above could be considered criminal. If the fine has not been paid, you will become the subject of criminal prosecution. The fine is applicable only in the case of a primary violation. In the case of second violation you will appear before the Supreme ………………………………….Please note: The fine may only be paid within 48 hours, if you let 48 hours pass without payment, the possibility of unlocking your computer expires. In this case a criminal case against you will be initiated automatically.”
How to remove ICE Cyber Crime Center Virus
Step 1. Download and burn “Hiren’s BootCD” into an optical disk.
1. From another computer, download “Hiren’s BootCD” .
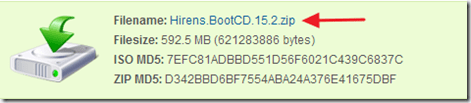
( Hiren’s BootCD Download page: http://www.hirensbootcd.org/download/
Scroll page down and click on “Hirens.BootCD.15.2.zip” )
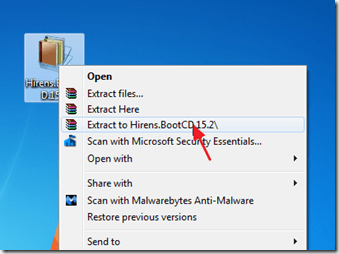
2. Right click on “Hirens.BootCD.15.2.zip” file and extract it.
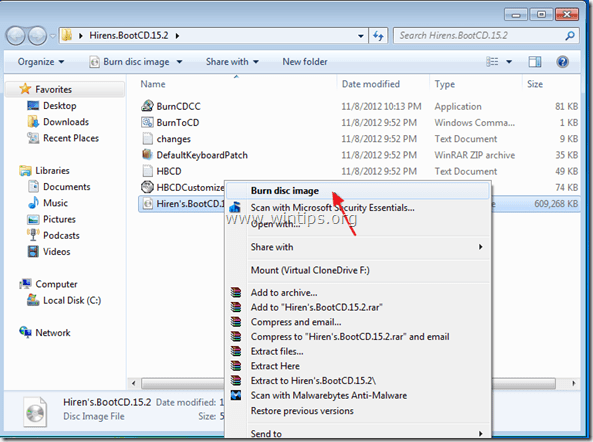
3. Inside “Hirens.BootCD.15.2” folder, find the “Hiren's.BootCD.15.2.ISO” disc image file and burn it to a CD.
Step 2: Boot the infected computer with Hirens.BootCD.
1. Take the CD out from the clean computer and insert it on the infected computer's CDROM drive.
2. Restart (Reset) the infected computer and boot from CD/DVD drive (Hiren’s CD).*
Notice*: First make sure that CD/DVD Drive is selected as the first boot device inside BIOS.
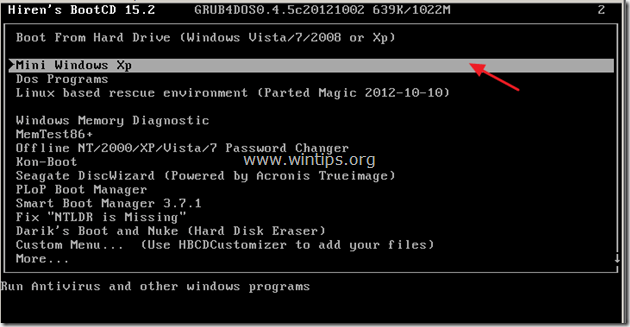
3. When the "Hiren’s BootCD” menu appears on your screen, use your keyboard arrows keys to move into the “Mini Windows Xp” option and then press "ENTER".
Step 3: Delete malicious files from the infected computer's hard disk.
Inside Mini Windows XP environment:
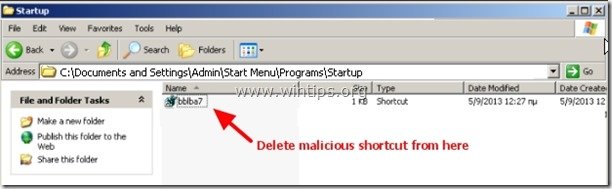
1. Navigate to the following paths and delete all malicious files/shortcuts from Windows Startup folder(s).
For Windows XP:
a. C:\Documents and Settings\<YOUR USERNAME>\Start Menu\Programs\Startup
b. C:\Documents and Settings\All Users\Start Menu\Programs\Startup
For Windows Vista or Windows 7:
a. C:\Users\Admin\<YOUR USERNAME>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
b. C:\Users\All Users\Microsoft\Windows\Start Menu\Programs\Startup
Malicious shortcut name(s):
“RandomName.lnk”
“RandomName.reg”
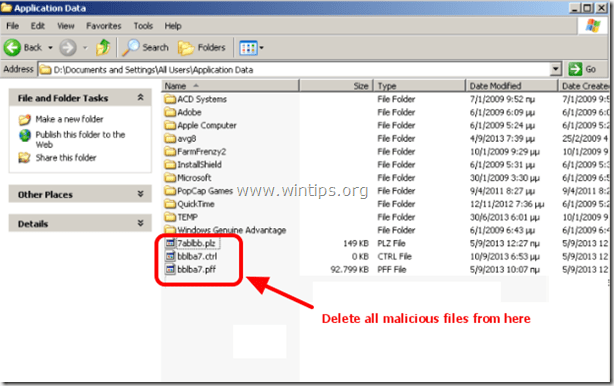
2. Navigate to the following paths and delete all malicious files* inside these folders:
For Windows XP:
a. C:\Documents and Settings\<YOUR USERNAME>\Application Data
b. C:\Documents and Settings\All Users\Application Data
For Windows Vista or Windows 7:
a. C:\Users\<YOUR USERNAME>\AppData\Roaming
b. C:\Users\<YOUR USERNAME>\AppData\Local
c. C:\Users\Default\AppData\Roaming
* Malicious file(s) name(s) example:
“RandomName” (e.g. 2433r433)
RandomName.DAT (e.g. data.DAT)
“RandomName.plz”
“RandomName.ctrl”
“RandomName.pff”
3. Finally delete all files and folders inside these folders:
a. C:\Users\<YOUR USERNAME>\AppData\Local\Temp\
b. C:\Windows\Temp\
4. Eject Hiren’s CD from your CD-drive and restart your computer.*
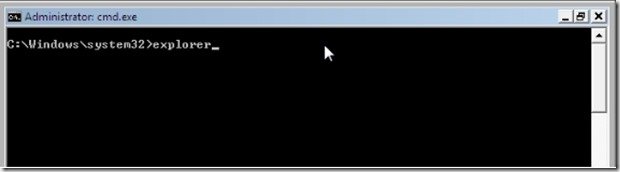
Important: * Normally you should log on to Windows without any lock problems. At this point, if your computer is stuck on a “Command Prompt” window and it doesn’t open Windows Explorer, then in command prompt, type “explorer” and press “Enter“.
Step 4. Prevent malicious programs running at Windows Startup.
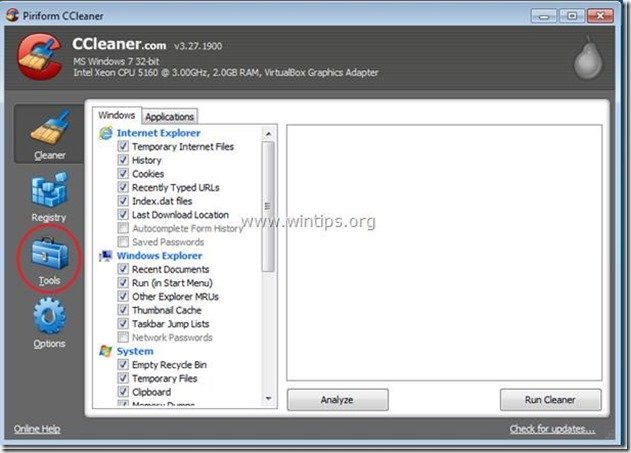
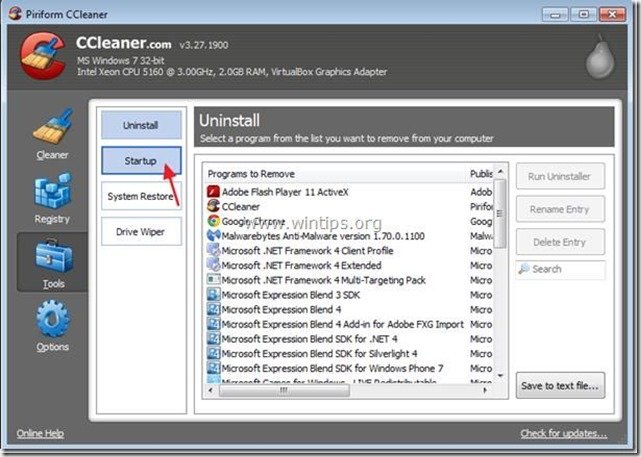
1. Download and run CCleaner.
2. At “CCleaner” main window, choose "Tools" on the left pane.
3. In "Tools" section, choose "Startup".
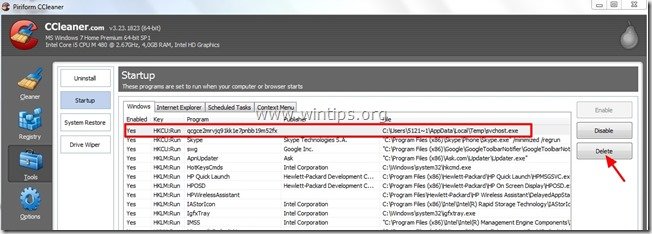
4. Choose "Windows” tab and then select and delete the following malicious entry, if it exists:
“C:\Users\<YOUR USERNAME>\AppData\Local\Temp\svchost.exe”
5. Close “CCleaner” and continue to the next step.
Step 5. Remove Winlogon Registry Values
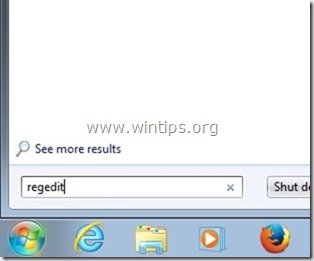
1. Go to Start > Run, type “regedit” and press “Enter”.
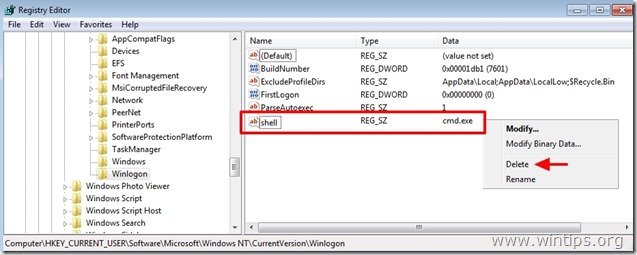
2. Delete the “shell REG_SZ cmd.exe” value from the following registry path:
“HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon”
3. Close registry editor and continue to the next step.
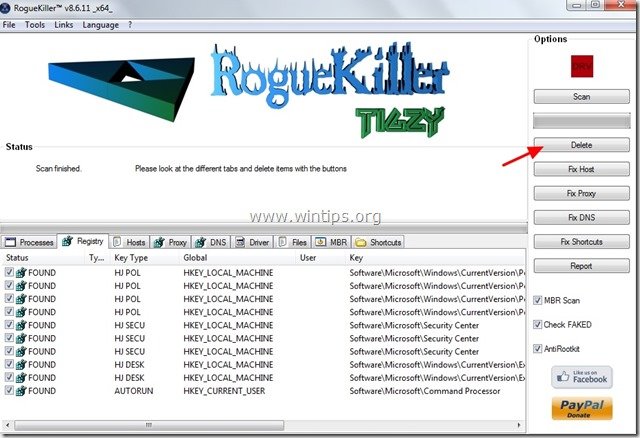
Step 6. Download RogueKiller.
1. Download and save "RogueKiller" utility on your computer'* (e.g. your Desktop).
Notice*: Download version x86 or X64 according your operating system’s version. To find your operating system's version, "Right Click" on your computer icon, choose "Properties" and look at "System Type" section.
2. Double Click to run RogueKiller.
3. Let the prescan to complete and then press on "Scan" button to perform a full scan.
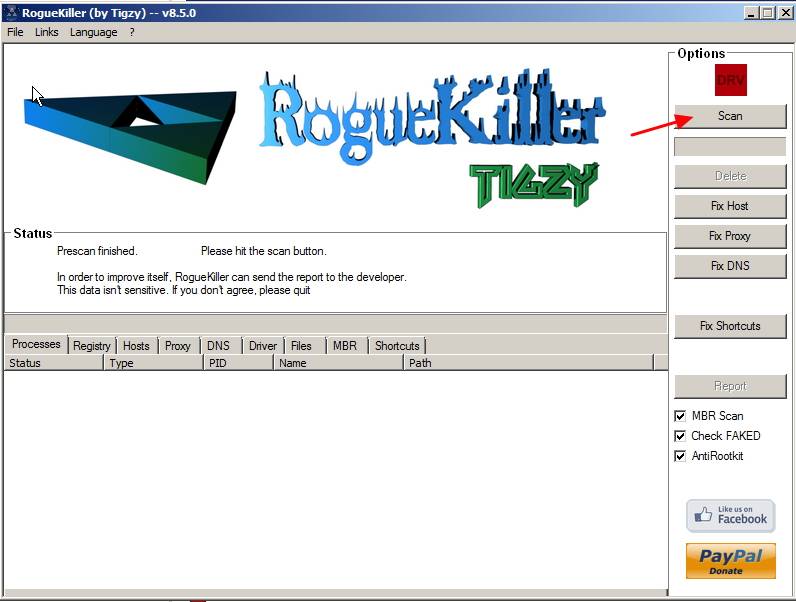
4. When the full scan is completed, press the "Delete" button to remove all malicious items found.
5. Restart your computer and continue to the next step.
Step 7: Clean remaining registry entries using “AdwCleaner”.
1. Download and save “AdwCleaner” utility to your computer.
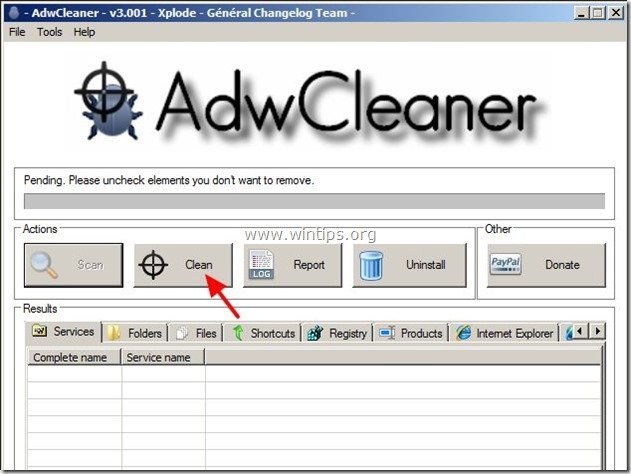
2. Close all open programs and Double Click to open ”AdwCleaner” from your computer.
3. Press “Scan”.
4. When the scan is completed, press “Clean” to remove all the unwanted malicious entries.
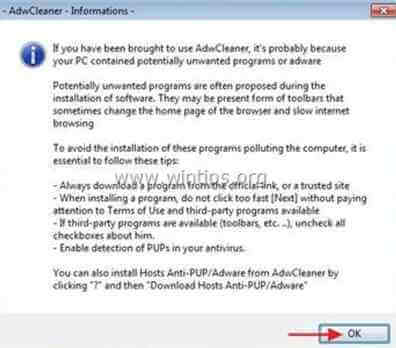
4. Press “OK” at “AdwCleaner – Information” and press “OK” again to restart your computer.
5. When your computer restarts, close "AdwCleaner" information (readme) window and continue to the next step.
Step 8. Clean your computer from remaining malicious threats.
Download and install one of the most reliable FREE anti malware programs today to clean your computer from remaining malicious threats. If you want to stay constantly protected from malware threats, existing and future ones, we recommend that you install Malwarebytes Anti-Malware PRO:
Malwarebytes™ Protection
Removes Spyware, Adware & Malware.
Start Your Free Download Now!
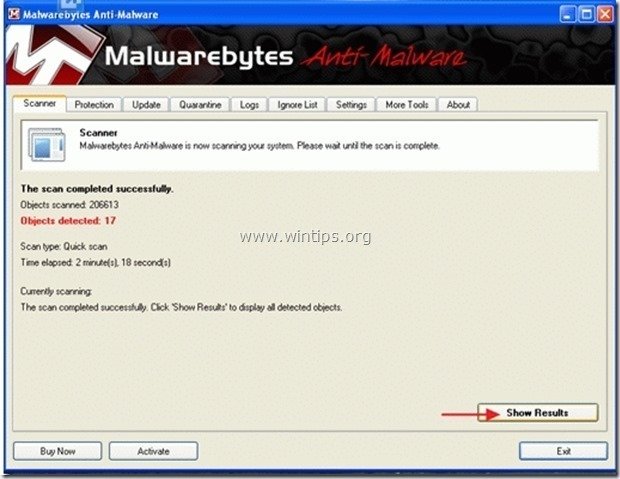
1. Run "Malwarebytes Anti-Malware" and allow the program to update to it's latest version and malicious database if needed.
2. When the "Malwarebytes Anti-Malware" main window appears on your screen, choose the default scanning option:
"Perform quick scan" and then choose "Scan" and let the program scan your system for threats.
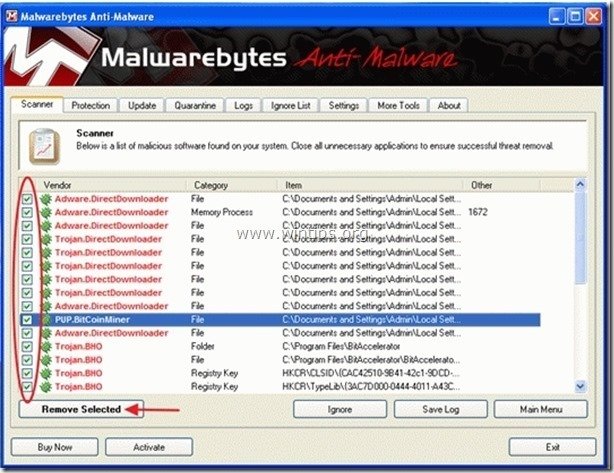
3. When the scanning is completed, press “OK” to close the information message and then press the "Show results" button to view and remove the malicious threats found.
4. At the "Show Results" window check – using your mouse's left button- all the infected objects and then choose the "Remove Selected" option and let the program remove the selected threats.
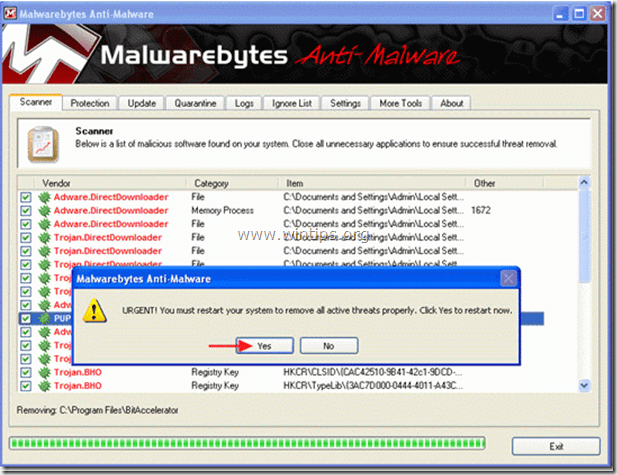
5. When the removal process of infected objects is complete, "Restart your system to remove all active threats properly".
6. Continue to the next step.
Advice: To ensure your computer is clean and safe, perform a Malwarebytes’ Anti-Malware full scan in windows “Safe mode“.*
*To get into Windows Safe mode, press the “F8” key as your computer is booting up, before the appearance of the Windows logo. When the “Windows Advanced Options Menu” appears on your screen, use your keyboard arrows keys to move to the Safe Mode option and then press “ENTER“.
Step 9. Clean unwanted files and entries.
Use “CCleaner” program and proceed to clean your system from temporary internet files and invalid registry entries.*
*If you don’t know how to install and use “CCleaner”, read these instructions.
Step 10. Restart your computer for changes to take effect and perform a full scan with your antivirus program.
We're hiring
We're looking for part-time or full-time technical writers to join our team! It's about a remote position that qualified tech writers from anywhere in the world can apply. Click here for more details.
- How to Disable Device Encryption in Windows 11. - April 17, 2024
- How to View Permissions on Shared Folders on Windows 10/11. - April 15, 2024
- FIX 0x80070643 error in KB5034441 update (Solved) - April 10, 2024



![malwarebytes-quick-scan_thumb2_thumb[1] malwarebytes-quick-scan_thumb2_thumb[1]](https://www.wintips.org/wp-content/uploads/2013/09/malwarebytes-quick-scan_thumb2_thumb1_thumb.jpg)