How to remove CryptoWall virus and restore your files
CryptoWall is another nasty ransomware virus that infects Windows Operating systems and it is the updated version of CryptoDefense ransomware virus. As a good ‘child’, it keeps its original abilities, as well as some new ones. CryptoWall encrypts all your files and keeps them locked and there is no way to use them until you pay the ransom asked. CryptoWall can encrypt all known file types (documents, PDF, photographs, videos and more) on all connected storage drives or locations. That means that it can infect (encrypt) all the files on the local or network drive(s), even in cloud storage systems (e.g. Google Drive, Dropbox, Box, etc.). Cryptowall does so, by adding strong encryption (RSA 2048) on each file. In simple words, you can’t open – or work with – your files anymore.
After Cryptowall infection, the virus creates several files on every infected folder named DECRYPT_INSTRUCTION.txt, DECRYPT_INSTRUCTION.html, and DECRYPT_INSTRUCTION.url which contain notes on how to pay the ransom in order to decrypt the encrypted files by following a specific procedure using Tor Internet Browser.
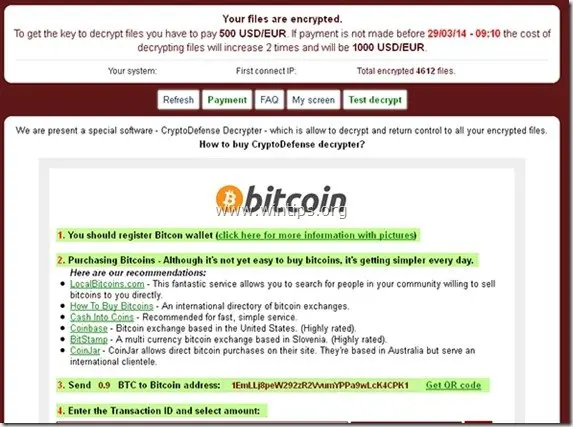
The Cryptowall’s ransom is set to 500$ (in BitCoins), if you pay it in the deadline period, otherwise the ransom will be increased at 1000$. After payment, hackers will sent you your private decryption key that can – supposedly – decrypt your files. The issue here is that even if you pay the ransom, you can’t be sure that your files will be restored. The only guarantee is that your money will go to some hacker that will keep doing the same thing to others victims.
The full CryptoWall information message is as follows:
“
What happened to your files ?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall.
More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them,
it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-2048 – public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
1.https://kpa2i8ycr9jxqwilp.torexplorer.com/xxxx
2.https://kpa2i8ycr9jxqwilp.tor2web.org/xxxx
3.https://kpa2i8ycr9jxqwilp.onion.to/xxxx
If for some reasons the addresses are not available, follow these steps:
1.Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en
2.After a successful installation, run the browser and wait for initialization.
3.Type in the address bar: kpa2i8ycr9jxqwilp.onion/xxxx
4.Follow the instructions on the site.
IMPORTANT INFORMATION:
Your personal page: kpa2i8ycr9jxqwilp.torexplorer.com/xxxx
Your personal page (using TOR): kpa2i8ycr9jxqwilp.onion/xxxx
Your personal identification number (if you open the site (or TOR 's) directly): xxxx
“
How to Prevent CryptoWall Infection.
- Precaution is always the safest way to keep your PC unharmed.
- You must be very careful whenever you open an unknown e-mail, especially if such an e-mail contains a fake notification (e.g. ‘UPS Exception Notification’) or .EXE, .SCR, or .ZIP file attachments.
- You must be careful in scam sites that prompt you to install software that you supposedly need and DO NOT INSTALL such software.
- The best way to deal with all type of malware infections is to always have a clean and as recent as possible backup of your important files stored in another OFFLINE (unplugged) medium (e.g. External USB HDD, DVD ROM, etc.). If you do that, you can first disinfect your computer and then restore all your files back from the clean backup.
Info: For this task I use a reliable smart and FREE (for personal use) backup software called “SyncBackFree”. A detailed article on how to use SyncBackFree to backup your important files can be found here. - Corporate network technicians can use a disk imaging software (like “Acronis True Image”) to take image backups of Workstations (or Servers) state at scheduled times. By doing that, the restore process is much easier and faster and is only limited from the storage you have available from the imaging process.
How to get your files back after Cryptowall infection.
Unfortunately, a FREE decryption tool or method to decrypt Cryptowall encrypted files DOES NOT EXIST (until the day this article was written – at the end of June 2014). So the only options you have to get your files back are the following:
- The first option is to pay the ransom*. After that, you will receive from the criminals your private decryption tool to decrypt your files.
* Note: If you decide to pay the ransom you have to do that at your own risk. Criminals are not the most trustworthy people in the world. - The second option is to disinfect your computer and then to restore your files from a clean backup (in case you have one).
- Finally, if you have a Windows 8, 7 or Vista OS and the “System Restore” feature was not disabled on your system (e.g. after a virus attack) then after disinfecting your system you can try to restore your files in previous versions from “Shadow Copies”. (See below on this article on how to do that).
How to remove Cryptowall virus and restore your files from Shadow Copies.
Part 1. How to remove Cryptowall infection.
Attention : If you want to remove Cryptowall infection from your computer, you must realize that your files will remain encrypted, even if you disinfect your computer from this nasty malware.
ONCE MORE: DO NOT CONTINUE TO REMOVE CRYPTOWALL VIRUS UNLESS:
YOU HAVE A CLEAN BACKUP COPY OF YOUR FILES STORED IN A DIFFERENT PLACE (like an unplugged portable hard disk drive.)
or
YOU DON”T NEED THE ENCRYPTED FILES BECAUSE THEY ARE NOT SO IMPORTANT TO YOU.
or
YOU WANT TO GIVE IT A TRY TO RESTORE YOUR FILES USING SHADOW COPIES FEATURE (Part 2 of this post).
So, if you have taken your final decision, then proceed, first to remove Cryptowall ransomware infection from your computer and then to try and restore your files by following the procedure below:
Step 1: Start your computer in “Safe Mode with Networking”
To do this,
1. Shut down your computer.
2. Start up your computer (Power On) and, as your computer is booting up, press the "F8" key before the Windows logo appears.
3. Using your keyboard arrows, select the "Safe Mode with Networking" option and press "Enter".
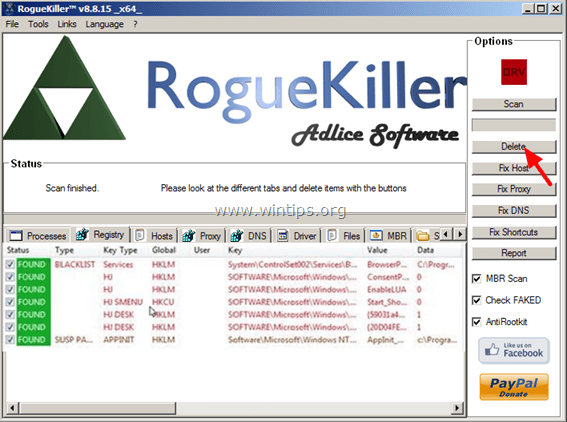
Step 2. Stop and delete Cryptowall running processes with RogueKiller.
RogueKiller is an anti-malware program designed to detect, stop & remove generic malwares and some advanced threats such as rootkits, rogues, worms, etc.
1. Download and save "RogueKiller" utility on your computer'* (e.g. your Desktop)
Notice*: Download version x86 or X64 according to your operating system's version. To find your operating system's version, "Right Click" on your computer icon, choose "Properties" and look at "System Type" section.
2. Double Click to run RogueKiller.
3. Wait until the pre-scan is completed and then read and “Accept” the license terms.
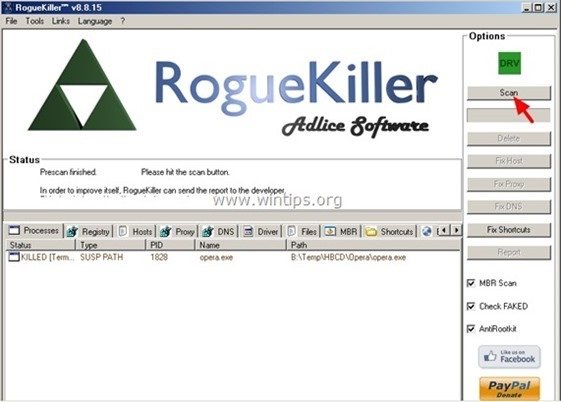
4. Press the “Scan” button to scan your computer for malicious threats and malicious startup entries.
5. Finally, when the full scan is completed, press the "Delete" button to remove all malicious items found.
6. Close “RogueKiller” and continue to the next step.
Step 3. Remove Cryptowall infection with Malwarebytes Anti-Malware Free.
Download and install one of the most reliable FREE anti malware programs today to clean your computer from remaining malicious threats. If you want to stay constantly protected from malware threats, existing and future ones, we recommend that you install Malwarebytes Anti-Malware Premium:
Malwarebytes™ Protection
Removes Spyware, Adware & Malware.
Start Your Free Download Now!
Quick download & Installation instructions:
- After you click the above link, press at the “Start My Free 14-Trial” option to start your download.
- To install the FREE version of this amazing product, uncheck the “Enable free Trial of Malwarebytes Anti-Malware Premium” option at the last installation screen.
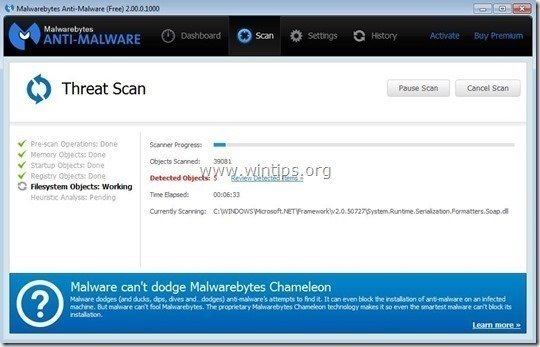
Scan & Clean your computer with Malwarebytes Anti-Malware.
1. Run "Malwarebytes Anti-Malware" and allow the program to update to its latest version and malicious database if needed.
2. When the update process is completed, press the “Scan Now” button to start scanning your system for malware and unwanted programs.
3. Now wait until Malwarebytes Anti-Malware finishes scanning your computer for malware.
4. When the scan has completed, first press the “Quarantine All” button to remove all threats found.
5. Wait until Malwarebytes Anti-Malware removes all infections from your system and then restart your computer (if required from the program) to completely remove all active threats.
6. After the system restarts, run Malwarebytes' Anti-Malware again to verify that no other threats remain in your system.
Part 2. How to restore Cryptowall encrypted files from Shadow copies.
After you have disinfected your computer from Cryptowall virus, then it is time to try to restore your files back to their state prior to the infection. There are two (2) methods to do that:
Method 1: Restore Cryptowall encrypted files using Windows “Restore Previous versions” feature.
Method 2: Restore Cryptowall encrypted files using ‘Shadow Explorer’ utility.
Attention: This procedure works only on latest operating systems (Windows 8, 7 & Vista) and only if the System Restore feature wasn’t previously disabled on the infected computer.
Method 1: How to restore Cryptowall encrypted files using “Previous versions” feature.
1. Navigate to the folder or the file that you want to restore in a previous state and right-click on it.
2. From the drop-down menu select “Restore Previous Versions”. *
3. Then choose a particular version of folder or file and then press the:
- “Open” button to view the contents of that folder/file.
- “Copy” to copy this folder/file to another location on your computer (e.g. your external hard drive).
- “Restore” to restore the folder file to the same location and replace the existing one.
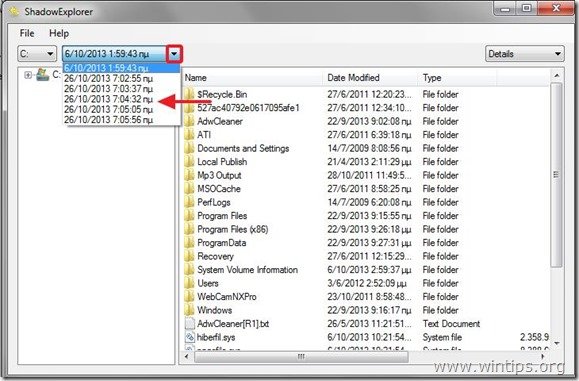
Method 2: How to restore Cryptowall encrypted files using “Shadow Explorer” utility.
ShadowExplorer, is a free replacement for the Previous Versions feature of Microsoft Windows Vista, 7, & 8 OS and you can use it to restore lost or damaged files from Shadow Copies.
1. Download ShadowExplorer utility from here. (You can either download the ShadowExplorer installer or the Portable version of the program).
2. Run ShadowExplorer utility and then select the date that you want to restore the shadow copy of your folder/files.
3. Now navigate to the folder/file that you want to restore to its previous version, right-click on it and select “Export”.
4. Finally specify where the shadow copy of your folder/file will be exported/saved (e.g. your Desktop) and press “OK”.
Good luck!.
We're hiring
We're looking for part-time or full-time technical writers to join our team! It's about a remote position that qualified tech writers from anywhere in the world can apply. Click here for more details.
- How to Disable or Remove BitLocker from Windows RE. - April 24, 2024
- FIX: Error 0x8007025d in Windows 10 Update. - April 22, 2024
- How to Disable Device Encryption in Windows 11/10. - April 17, 2024

![safe-mode-with-networking_thumb1_thu[1] safe-mode-with-networking_thumb1_thu[1]](https://www.wintips.org/wp-content/uploads/2013/10/safe-mode-with-networking_thumb1_thu1_thumb.jpg)

![malwarebytes-downlaod_thumb1_thumb2_[1] malwarebytes-downlaod_thumb1_thumb2_[1]](https://www.wintips.org/wp-content/uploads/2014/05/malwarebytes-downlaod_thumb1_thumb2_1_thumb4.jpg)
![malwarebytes-anti-malware-free-insta[2] malwarebytes-anti-malware-free-insta[2]](https://www.wintips.org/wp-content/uploads/2014/05/malwarebytes-anti-malware-free-insta2_thumb3.jpg)
![update-malwarebytes-anti-malware_thu[1] update-malwarebytes-anti-malware_thu[1]](https://www.wintips.org/wp-content/uploads/2014/05/update-malwarebytes-anti-malware_thu1_thumb2.jpg)
![start-scan-malwarebytes-anti-malware[2] start-scan-malwarebytes-anti-malware[2]](https://www.wintips.org/wp-content/uploads/2014/05/start-scan-malwarebytes-anti-malware2_thumb2.jpg)

![wwrq1ctw_thumb1_thumb_thumb_thumb_th[2] wwrq1ctw_thumb1_thumb_thumb_thumb_th[2]](https://www.wintips.org/wp-content/uploads/2014/05/wwrq1ctw_thumb1_thumb_thumb_thumb_th2_thumb1.jpg)


![ShadowExplorer export[5] ShadowExplorer export[5]](https://www.wintips.org/wp-content/uploads/2013/10/ShadowExplorer-export5_thumb.jpg)




May 16, 2016 @ 8:27 am
My Com infect RSA4096, Roguekiller & shadow explorer won't work, i use spyhunter to kill than use mini tool power data recovery to get my photo back. for those infect RSA4096 with work.
March 24, 2016 @ 11:20 pm
Hi, I wanted to say thank you also! I was able to remove it fairly quickly by myself, Malwarebytes is always my go to in these cases. But the file recovery was more difficult. Ontrack and programs like that got me nowhere (all files corrupted) and previous versions didn't work either. Then I found this and tried shadow explorer! That worked like a charm!
Luckily for me, the infected computer (my mothers) was detected within hours because it started messing with a shared Dropbox folder, which promted messages on my computer. Now I just need to find a way to prevent programs like this from messing with my backups in Dropbox and Google Drive, now that this type of thing is starting up again. If anyone has any ideas, please let me know!
January 7, 2016 @ 4:23 pm
Hello! I have encountered this virus and i managed to remove it by following your steps. I didn't loose any important files.
I'm writing only to intend to thank you for doing such a great job in order to help us.
October 29, 2015 @ 2:37 pm
Hi, I am trying to recover my files with Shadow Explorer, but it shows me previous versions of my files from a week ago. My computer has been infected about 4 weeks ago. :(
Is it any other way to recover my files?
Warm regards
November 5, 2015 @ 11:10 am
@Gratiela: Unfortunately, (as i know so far) no.
December 20, 2015 @ 2:37 pm
Hello Mark, I am with Windows XP and I have the same problem like you. Could you restore your files?
September 20, 2015 @ 9:07 am
This is the most horrible experience one will endure, I don't wish this on my worst enemy, good luck all, keep the posts coming maybe someone might find a solution, we hope and we pray, I just got infected myself and I am looking for a solution, I am on win Xp as well and will re-post if I find anything useful. Thank you all for helping out.
October 7, 2015 @ 11:39 am
Hi bob,
There are many different variants out there currently. Ive had luck with recovering some machines by using a tool like Recuva. this does a deep scan and retrieves deleted files. Some of the variants perform a copy/rename of the file, encrypt the file and delete the original, so sometimes you can restore using above said programs.
A good working backup is your safest bet.
Unfortunately the master servers sit in the Tor network so it makes it very difficult to hack the bastards. :( doesn't stop me trying but.
August 28, 2015 @ 8:36 am
Dear All,
A few days ago, my laptop was attacked by above virus and I am now trying to find a solution. Since the last post above is dated Apr 15, I am wondering if anybody has come across any other solution ? Did anyone try the procedure mentioned by Cal (i.e.
take the hard drive out, put it in another machine as external drive and run a file recovery program) ? Many thanks in advance.
August 28, 2015 @ 2:52 am
what if I installed a new windows version and deleted all the encrypted files .. would this help??
August 29, 2015 @ 9:01 am
@Menna: If you format your drive during installation, you will clean the virus, but you will completely lose your data.
April 23, 2015 @ 8:05 pm
Just curious I helped a friend remove virus but he has winxp so restoration options you describe above don't apply. Can we restore his computer to factory settings or are they also encrypted?
thanks in advance
April 24, 2015 @ 7:39 am
@evelyn raynond: The factory settings are not encrypted. Factory settings doesn't restore your personal (encrypted) files, only the OS as installed by manufacturer.
April 8, 2015 @ 6:16 pm
Hi i got same virus, and i dont have anything important on my computer, can I just install new Windows? Than virus is gone for sure, right? Please answer as soon as possible, because my internet operator block my connection because that stupid virus. Thank you in advance :)
April 9, 2015 @ 7:30 am
@vladimir: If you clear the virus you haven't to re-install Windows.
March 17, 2015 @ 3:14 pm
i am running windows xp and this happened to my computer.
i do not have a backup of my files.
will the shadow work to restore my files running window xp?
March 17, 2015 @ 3:34 pm
@mark: Unfortunately not. It's designed to work on Windows Vista/7 and it seems to work on Windows Server 2003/2008/2008 R2 aswell.
December 21, 2015 @ 12:36 pm
Mark, I am with Windows XP and I have the same problem like you. Could you restore your files?
March 14, 2015 @ 10:32 am
Before doing this i re installed the win 7 OS…. after tat i tried this steps but i cant get the previous version of the folder… plz help me
March 14, 2015 @ 10:55 am
@Suren: Unfortunately, you have deleted all previous versions during re-install.
March 14, 2015 @ 11:54 am
i cant get my files back?
March 14, 2015 @ 2:14 pm
You cannot…
March 5, 2015 @ 4:06 am
Hi i have a question. After the infection, if i send my "not attacked document" in my computer to external hard disk, are there any possibility that the external hard disk is also infected?
(Sorry for my poor english)
March 5, 2015 @ 2:09 pm
@Hwang: If you have already disinfect your computer then there is no problem.
February 24, 2015 @ 8:14 am
just did it .had the drive as external and use shadow restored everything
thank you
February 3, 2015 @ 10:59 am
I've cleaned it all. But i don't have any "restore previous version" sellection. Also from shadow explorer, it's just a blank page. What's wrong? Is it because i don't have a restore point? Or my recovery option deactivated? Any other way to restore my files?
February 3, 2015 @ 11:48 am
For some reason System Restore is disabled on your computer. Unfortunately -as I know- there is no other way to restore your files, but some people (online) reported that by using a file recovery program (e.g. Ontrack EasyRecovery, R-Studio or Easeus Data Recovey) managed to regain their files.
January 30, 2015 @ 2:16 pm
since i am facing the same problem of the cryptowall virus i trued all the methods and finally i formatted and installed the os it is possible to decrypt or recover my word and xl files if so pls suggest me how to do it
January 28, 2015 @ 3:51 pm
Hi, thanks for the article. I have a question – I have all my photographs on an external hard drive and they have all been "attacked" by this scourge. Is there any way that I would be able to recover them? all are .jpeg files.
January 29, 2015 @ 7:26 pm
@Barbara: Unfortunately, there is not!
December 30, 2014 @ 9:44 pm
Nice article, I found the following file recovery solution on another website and want to know if you have heard of it and if it works. Thanks in advance! Cal
——————————————————————————————————–
What if you have no shadow copies and no backup of your files ? There is still a way.
As I said, Cryptowall doesn’t encrypt your original files. It will do a copy of it, encrypt it, and delete the original file.
As you probably know, a deleted file can be recover if nothing as been written over it on your disk. Good think you quickly power off the machine soon after the infection !
Now all you have to do is take your hard drive out, put it in another machine as external drive, or second drive if you don’t have a sata dock, an run a file recovery program.
I use Ontrack EasyRecovery or R-Studio, or even DataRescue for Mac.
The pro version of Ontrack EasyRecovery might also be able to recover files from a RAID array if one of your network share as been encrypted and you don’t have backups.
All these programs will be able to recover the original files deleted by Cryptowall.
Just make sure when you run those to NOT do it directly on the original machine as by writing on your infected disk, the program could Overwrite your deleted files.
You should be able to recover 99% of your files using this method.
January 31, 2015 @ 6:34 pm
THANK YOU CAL i have data in my other drive and formatted c drive now can i copy the data to pendrive or external hd and try to recover in my computer itself pls help me Bro.
December 19, 2014 @ 4:00 pm
I can not open shadow explorer after downloading it. I get an error message. I have win 8 and my files is on dropbox. How can I recover them from dropbox
December 19, 2014 @ 6:57 pm
You cannot recover files from dropbox using Shadow Explorer. Look here on how to restore previous versions from Dropbox: https://www.dropbox.com/help/11
December 7, 2014 @ 1:28 pm
after exporting my files (with shadow explorer) to another disk, is it really safe to open them on another computer? I mean, there is no risk of exporting the infection?
December 8, 2014 @ 10:23 am
If you already clean your computer & scan files with AV program, there is no risk!
December 3, 2014 @ 11:27 am
Using Shadow Explorer would it be safe to export my desktop folder? All docs and most of the photos I want to recover are on the desktop.. help please.
December 3, 2014 @ 12:50 pm
Yes it is safe. But recover (extract) them to another disk.
December 2, 2014 @ 11:11 pm
I think I picked up the cryptowall thing about a month ago, I first noticed I could not open files then noticed the decrypt_instruction.txt on the desktop. Not knowing what I know now, I just started deleating everythig that said anything adout decrypt…I never was directed to the BITCOIN webpage deal. I have since run Malwarebvtes and Spyhunter, now I want to try to recover some of my files with this Shadow Explorer … any further advice?? Thanks!!
December 3, 2014 @ 9:55 am
@ Robert. Good luck. All I know about cryptowall are already mentioned here.
November 14, 2014 @ 5:59 am
i have windows xp please help
November 14, 2014 @ 6:02 pm
Unfortunately there is not a working solution (yet) for Windows XP.
November 12, 2014 @ 2:12 am
What if I don't care about the files that are encrypted? Can I simply delete them all? Or is the cryptowall still in there and will affect future files that I may put onto the computer?
November 12, 2014 @ 10:15 am
Yes you can delete your files. But first you have to disinfect your computer.
November 11, 2014 @ 12:50 am
Is there a way to restore quickbooks with shadow explorer.. or any other known site/download for that matter. I would hate to have a years worth of things to search for and find since I did not complete the backup.. eeeeek!!!
November 3, 2014 @ 7:55 am
When restoring files from a clean backup, is it safe to overwrite the encrypted versions?
November 3, 2014 @ 11:43 am
Yes, it's safe. (but first disinfect you computer).
September 30, 2014 @ 7:21 am
I use Windows XP. I have successfully removed the viruses, but how can I restore my files?
September 30, 2014 @ 11:03 am
Only from a clean backup.
September 25, 2014 @ 12:37 am
Is there a known signature that you can search for within your environment to determine if the virus came through email, or is attached to a file that might be on a fileshare?
September 25, 2014 @ 10:55 am
As i know, there isn't a known signature.
September 20, 2014 @ 6:56 pm
Using the guidance from this site, I was able to successfully remove the cryptowall and used ShadowExplorer to restore my files. It was a bit tedious but well worth the time to restore all. Thank you so much for the guidance.
September 11, 2014 @ 8:44 pm
Hi:
Nice article, I read that there is a way to decrypt your files as of the END of JUNE 2014. Can you help me understand how we decrypt our files?
Thank you,
Helpdesk
September 12, 2014 @ 7:50 am
I'm sorry, misunderstanding… 'Unfortunately, a FREE decryption tool or method to decrypt Cryptowall encrypted files DOES NOT EXIST (until the day this article was written – at the end of June 2014).'