How to remove "Desk 365" Malware application virus (Removal Instructions)
“Desk 365” is a malicious application and is categorized as a potentially unwanted program (PUP). As "Potentially Unwanted Programs" are categorized all the programs that can potentially harm your computer. These types of programs in most cases are installed on the computer according to user permission because they are bundled inside free software that the user wants to install.
"PUPs" may include adware, toolbars, spyware or dialers in their code and for that reason users must pay attention when installing free software on their computers. PUPs may run in the computer's background in order to make your computer insecure to viruses or remote computer attacks.
When "Desk 365” is installed on your computer, the computer speed is slowed down, the Web browser performs browsing redirects when you search the Internet or it displays results and advertisements from unknown publishers.
To uninstall “Desk 365” from your computer & restore your browser search settings, follow the steps below:
How to remove "Desk 365” from your computer
Step 1. Stop and clean malicious running processes.
1. Download and save "RogueKiller" utility on your computer'* (e.g. your Desktop).
Notice*: Download version x86 or X64 according to your operating system's version. To find your operating system's version, "Right Click" on your computer icon, choose "Properties" and look at "System Type" section.
2. Double Click to run RogueKiller.
3. Let the prescan to complete and then press on "Scan" button to perform a full scan.
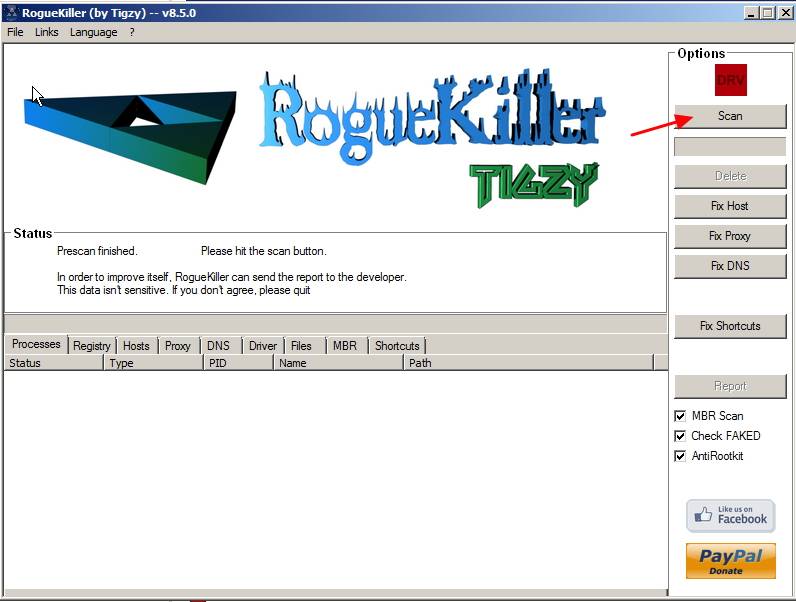
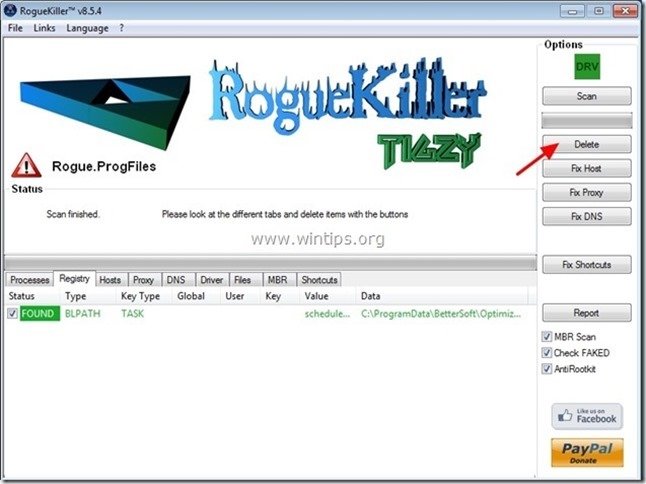
3. When the full scan is completed, navigate to all tabs to select and "Delete" all malicious items found.
Step 2. Uninstall “Desk 365” unwanted software from your computer.
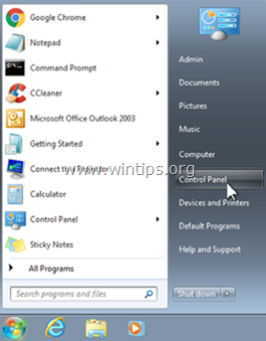
1. To do this, go to:
- Windows 8/7/Vista: Start > Control Panel.
- Windows XP: Start > Settings > Control Panel
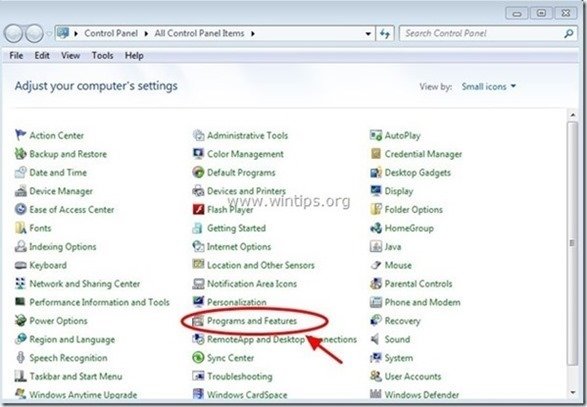
2. Double click to open
- Add or Remove Programs if you have Windows XP
- Programs and Features if you have Windows 8, 7 or Vista.
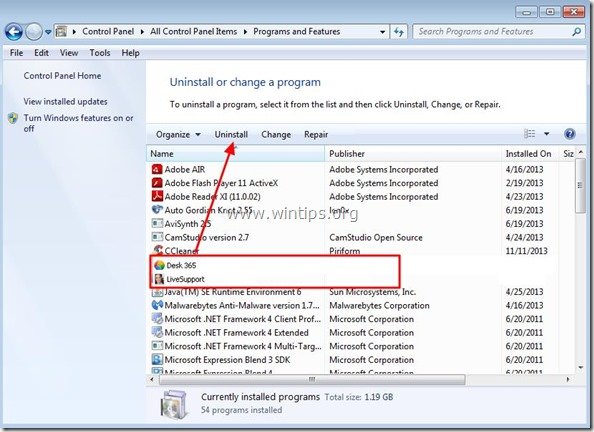
3. In the program list, find and Remove (Uninstall) these applications :
- Desk 365 (Pc Utilities Software Limited) *
- Live Support (337 Technology Limited)
- FilesFrog Updater Checker
- Bundled Software Uninstaller
- Any other unknown application like: “Wsys Control”, “Optimizer Pro”, iLivid etc..
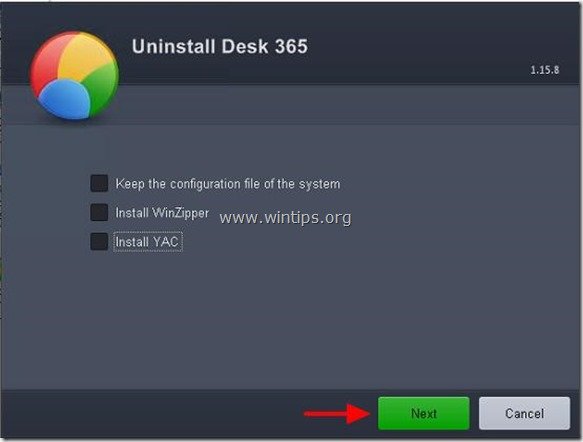
* At “Desk 365” uninstall window, uncheck all checkboxes and press “Next”.
Step 3: Clean Adware & Malicious registry entries using “AdwCleaner”.
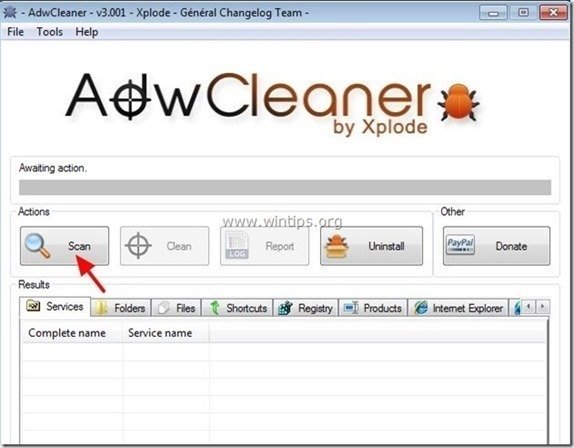
1. Download and save “AdwCleaner” utility to your desktop.
2. Close all open programs and Double Click to open ”AdwCleaner” from your desktop.
3. Press “Scan”.
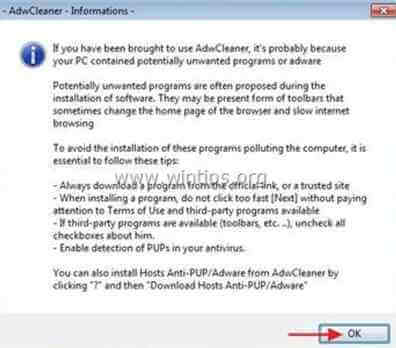
4. When the scan is completed, press “Clean” to remove all the unwanted malicious entries.
4. Press “OK” at “AdwCleaner – Information” and press “OK” again to restart your computer.
5. When your computer restarts, close "AdwCleaner" information (readme) window and continue to the next step.
Step 4. Remove potentially unwanted programs (PUPs) with Junkware Removal Tool.
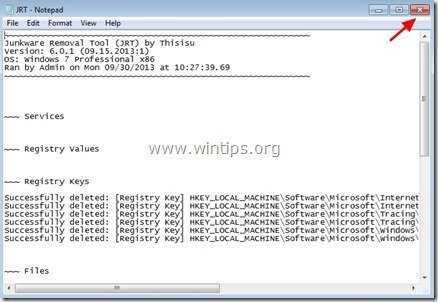
1. Download and run JRT – Junkware Removal Tool.
2. Press any key to start scanning your computer with “JRT – Junkware Removal Tool”.
3. Be patient until JRT scans and cleans your system.
4. Close JRT log file and and then reboot your computer.
Step 5. Clean your computer from remaining malicious threats.
Download and install one of the most reliable FREE anti malware programs today to clean your computer from remaining malicious threats. If you want to stay constantly protected from malware threats, existing and future ones, we recommend that you install Malwarebytes Anti-Malware PRO:
Malwarebytes™ Protection
Removes Spyware, Adware & Malware.
Start Your Free Download Now!
1. Run "Malwarebytes Anti-Malware" and allow the program to update to it's latest version and malicious database if needed.
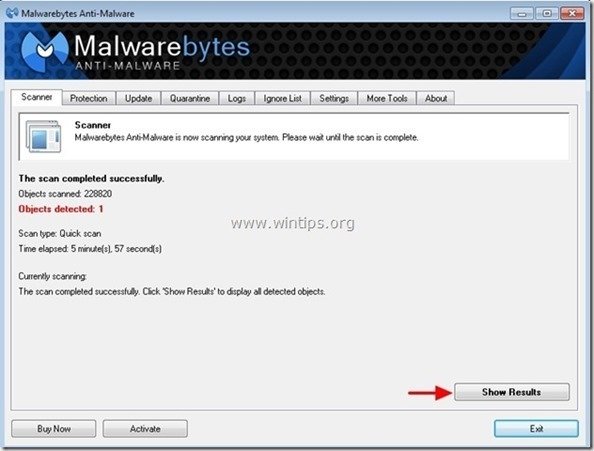
2. When the "Malwarebytes Anti-Malware" main window appears on your screen, choose the "Perform quick scan" option and then press "Scan" button and let the program scan your system for threats.
3. When the scanning is completed, press “OK” to close the information message and then press the "Show results" button to view and remove the malicious threats found.
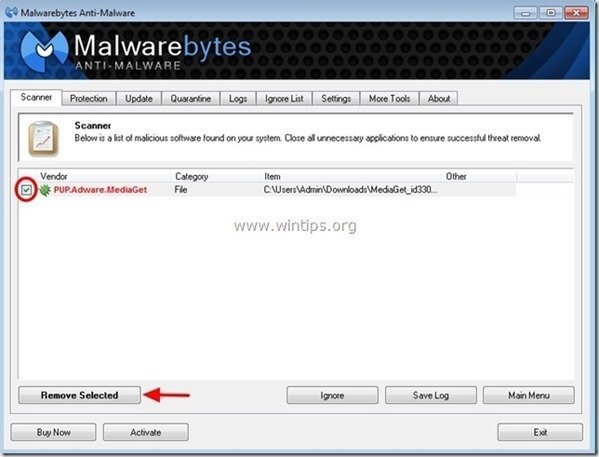
4. At the "Show Results" window check – using your mouse's left button- all the infected objects and then choose the "Remove Selected" option and let the program remove the selected threats.
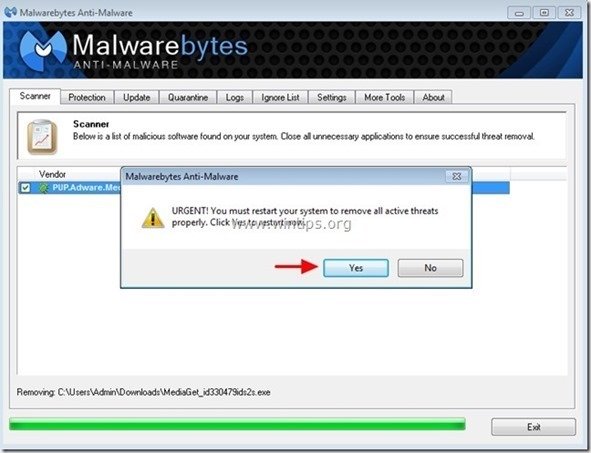
5. When the removal of infected objects process is complete, "Restart your system to remove all active threats properly"
6. Continue to the next step.
Advice: To ensure your computer is clean and safe, perform a Malwarebytes’ Anti-Malware full scan in windows “Safe mode“.*
*To get into Windows Safe mode, press the “F8” key as your computer is booting up, before the appearance of the Windows logo. When the “Windows Advanced Options Menu” appears on your screen, use your keyboard arrows keys to move to the Safe Mode option and then press “ENTER“.
Step 6. Clean unwanted files and entries.
Use “CCleaner” program and proceed to clean your system from temporary Internet files and invalid registry entries.*
*If you don’t know how to install and use “CCleaner”, read these instructions.
We're hiring
We're looking for part-time or full-time technical writers to join our team! It's about a remote position that qualified tech writers from anywhere in the world can apply. Click here for more details.
- How to Disable or Remove BitLocker from Windows RE. - April 24, 2024
- FIX: Error 0x8007025d in Windows 10 Update. - April 22, 2024
- How to Disable Device Encryption in Windows 11/10. - April 17, 2024

![adwcleaner-clean_thumb1_thumb_thumb_[1] adwcleaner-clean_thumb1_thumb_thumb_[1]](https://www.wintips.org/wp-content/uploads/2013/11/adwcleaner-clean_thumb1_thumb_thumb_1_thumb.jpg)



![ahefjplu_thumb2_thumb_thumb_thumb_th[1] ahefjplu_thumb2_thumb_thumb_thumb_th[1]](https://www.wintips.org/wp-content/uploads/2013/11/ahefjplu_thumb2_thumb_thumb_thumb_th1_thumb.jpg)