How to remove CryptoLocker Ransomware and Restore your files
Cryptolocker (also known as “Troj/Ransom-ACP”, “Trojan.Ransomcrypt.F”) is a Ransomware software that when it infects your computer, it encrypts all the files in it. The bad news with this virus is that, once it infects your computer, your critical files are encrypted with strong encryption and it is practically impossible to decrypt them.
The Cryptolocker Ransomware demands that you make a payment of 300$ or 300€ in a specific period of time (e.g. 72h or 100h), through a payment service (e.g. MoneyPak, Ukash, PaySafeCard, etc.) in order to unlock your files. otherwise -after that period- nobody can restore or decrypt them.
The Cryptolocker is not a virus, but a malware software and it probably infects your computer when you open an email attachment from a legitimate sender that seems innocent or from your network shares or from an external USB drive that was plugged on your computer.
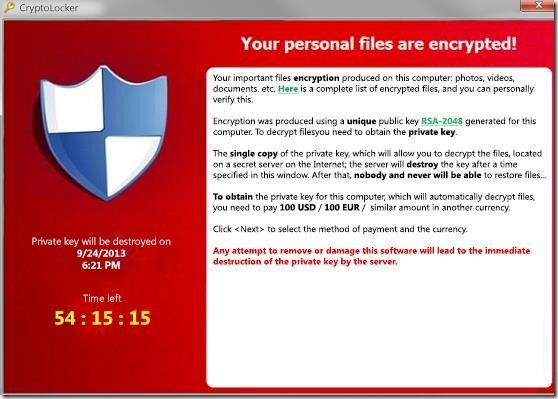
Once Cryptolocker infects your computer, it starts to encrypt all personal files on your computer and then it sends the decryption key – known as “CryptoLocker ID” – to an online server. When Cryptolocker finishes encrypting your files, then a notification message comes on your screen demanding an immediate payment to unlock them. The message informs you that “Your personal files have been encrypted and you have 72 hours to pay us 300$”.
From our research on several sites, we can inform our readers that in some cases, the files remain encrypted, despite the fact that the user makes the payment. So make this decision (to pay to unlock your files) at your own risk. The other choice is to remove CryptoLocker Ransomware infection from your computer, but in this case, you must realize that your files will remain encrypted, even if you disinfect your computer from this nasty malware. If you take this decision (to disinfect your computer) the only way to restore your files is from shadow copies by using Windows' “Restore previous versions” feature found at the latest operating systems.
Update: (August 2014): FireEye & Fox-IT have released a new service that retrieves the private decryption key for users that were infected by the CryptoLocker ransomware. The service is called 'DecryptCryptoLocker', (the service has discontinued) it is available globally and does not require users to register or provide contact information in order to use it.
In order to use this service you have to visit this site: (the service has discontinued) and upload one encrypted CryptoLocker file from the infected computer (Notice: upload a file that doesn’t contain sensitive and/or private information). After you do that, you have to specify an email address in order to receive your private key and a link to download the decryption tool. Finally run the downloaded CryptoLocker decryption tool (locally on your computer) and enter your private key to decrypt your CryptoLocker encrypted files.
More information about this service can be found here: FireEye and Fox-IT Announce New Service to Help CryptoLocker Victims.
ONCE MORE: DO NOT CONTINUE TO REMOVE CRYPTOLOCKER VIRUS UNLESS:
YOU HAVE A CLEAN BACKUP COPY OF YOUR FILES STORED IN A DIFFERENT PLACE (like an unplugged portable hard disk)
or
YOU DON”T NEED THE ENCRYPTED FILES BECAUSE THEY ARE NOT SO IMPORTANT TO YOU.
or
YOU WANT TO GIVE IT A TRY TO RESTORE YOUR FILES USING SHADOW COPIES FEATURE (Step 5).
So, if you have taken your final decision, then proceed first to remove Cryptolocker Ransomware infection from your computer and then try to restore your files by following the steps bellow:
How to get rid of CryptoLocker RansomWare & Restore Cryptolocker Encrypted files.
CryptoLocker RansomWare Removal Guide
Step 1: Start your computer in “Safe Mode with Networking”
Windows 7, Vista & XP users:
1. Shut down your computer.
2. Start up your computer (Power On) and, as your computer is booting up, press the "F8" key before the Windows logo appears.
3. Using your keyboard arrows select the "Safe Mode with Networking" option and press "Enter".
Windows 8 & 8.1 users*:
* Also works in Windows 7, Vista & XP.
1. Press “Windows” ![]() + “R” keys to load the Run dialog box.
+ “R” keys to load the Run dialog box.
2. Type “msconfig” and press Enter.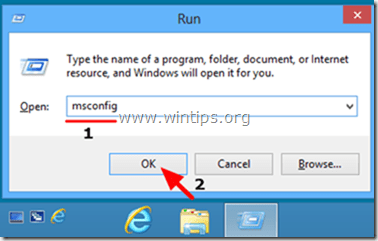
3. Click the Boot tab and check “Safe Boot” & “Network”.
4. Click “OK” and restart your computer.
Note: In order to boot Windows in “Normal Mode” again, you have to uncheck the “Safe Boot” setting by using the same procedure.
Step 2. Stop and clean malicious running processes.
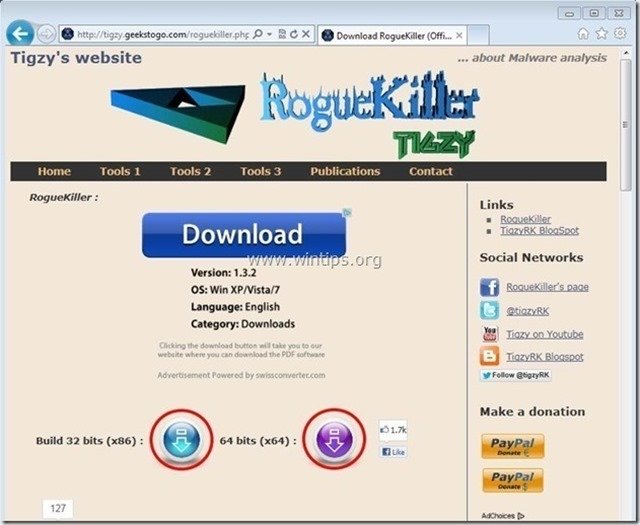
1. Download and save "RogueKiller" utility on your computer'* (e.g. your Desktop)
Notice*: Download version x86 or X64 according to your operating system's version. To find your operating system's version, "Right Click" on your computer icon, choose "Properties" and look at "System Type" section
2. Double Click to run RogueKiller.
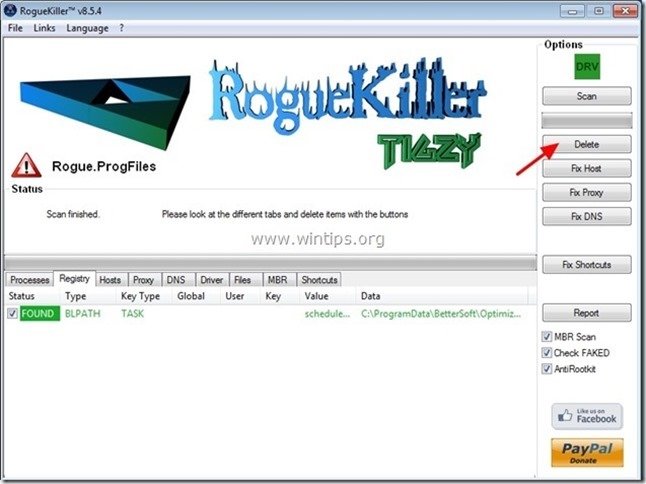
3. Let the prescan to complete and then press on "Scan" button to perform a full scan.
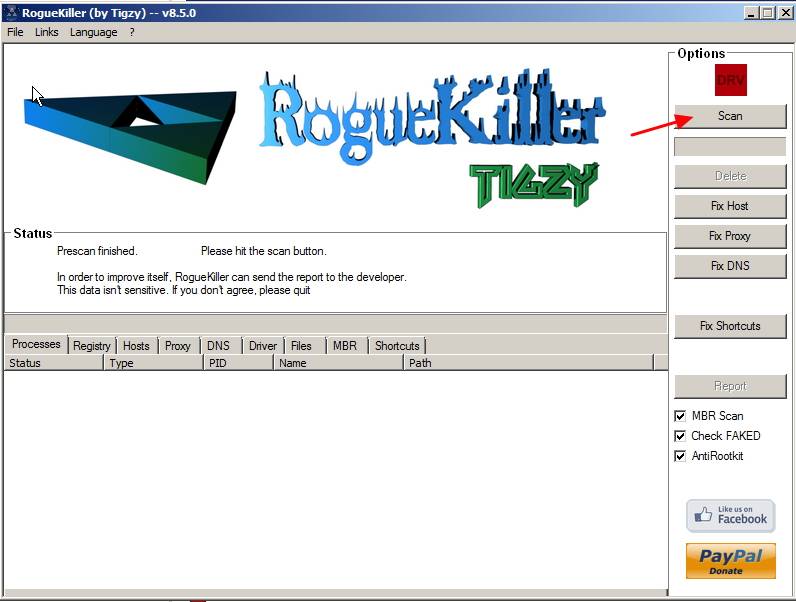
3. When the full scan is completed, press the "Delete" button to remove all malicious items found.
4. Close RogueKiller and proceed to the next Step.
Step 3. Clean your computer from remaining malicious threats.
Download and install one of the most reliable FREE anti malware programs today to clean your computer from remaining malicious threats. If you want to stay constantly protected from malware threats, existing and future ones, we recommend that you install Malwarebytes Anti-Malware PRO:
Malwarebytes™ Protection
Removes Spyware, Adware & Malware.
Start Your Free Download Now!
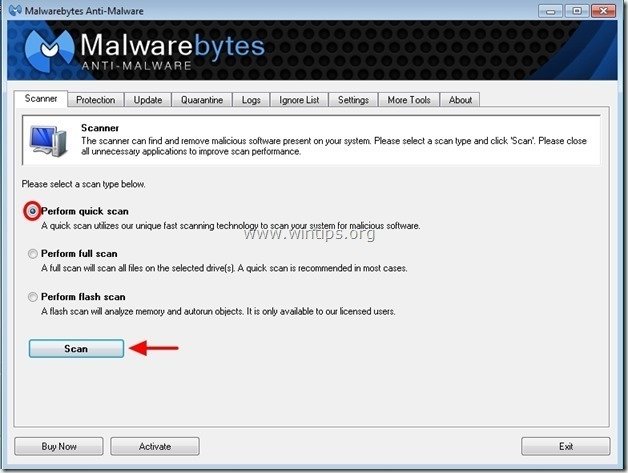
1. Run "Malwarebytes Anti-Malware" and allow the program to update to it's latest version and malicious database if needed.
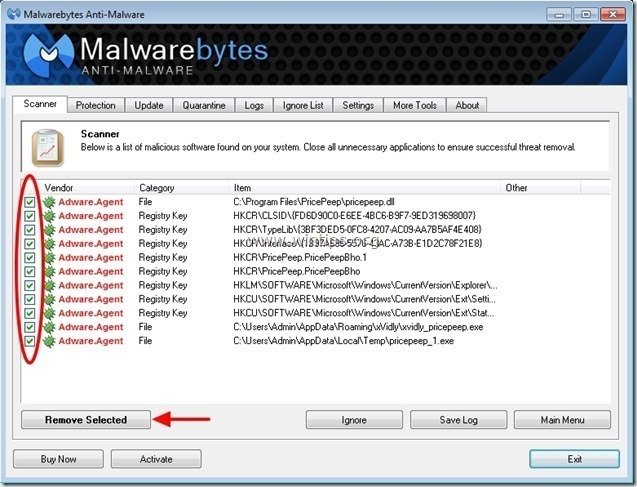
2. When the "Malwarebytes Anti-Malware" main window appears on your screen, choose the "Perform quick scan" option and then press "Scan" button and let the program scan your system for threats.
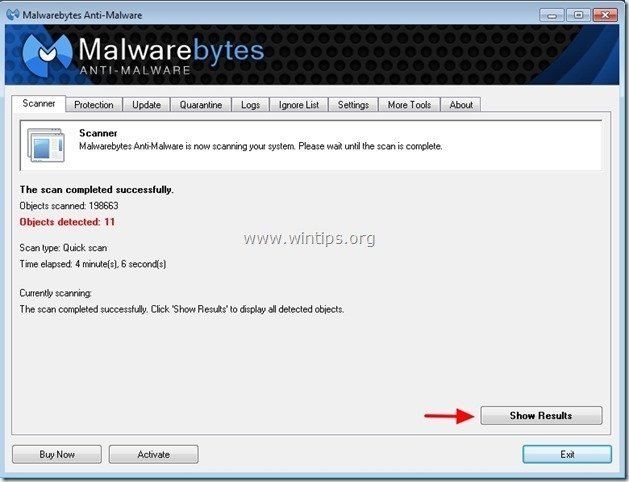
3. When the scanning is completed, press “OK” to close the information message and then press the "Show results" button to view and remove the malicious threats found.
4. At the "Show Results" window check – using your mouse's left button- all the infected objects and then choose the "Remove Selected" option and let the program remove the selected threats.
5. When the removal of infected objects process is complete, "Restart your system to remove all active threats properly"
6. Continue to the next step.
Step 4. Delete Cryptolocker Ransomware hidden files.
Notice: You must enable the hidden files view to perform this task.
1. Navigate to the following paths and delete all Cryptolocker Hidden files:
For Windows XP:
- C:\Documents and Settings\<YOUR USERNAME>\Application Data\RandomFileName.exe
e.g. {DAEB88E5-FA8E-E0D1-8FCD-BFC7D2F6ED25}.exe
- C:\WINDOWS\system32\msctfime.ime
For Windows Vista or Windows 7:
- C:\Users\<YOUR USERNAME>\AppData\Roaming\RandomFileName.exe
e.g. {DAEB88E5-FA8E-E0D1-8FCD-BFC7D2F6ED25}.exe
- C:\WINDOWS\system32\msctfime.ime
2. Finally delete all files and folders under your TEMP folders:
For Windows XP:
- C:\Documents and Settings\<YOUR USERNAME>\Local Settings\Temp\
- C:\Windows\Temp\
For Windows Vista or Windows 7:
- C:\Users\<YOUR USERNAME>\AppData\Local\Temp\
- C:\Windows\Temp\
Restore your files from Shadow Copies.
Step 5. Restore your files after Cryptolocker Infection
After you have disinfected your computer from Cryptolocker virus, then it is time to try to restore your files back to their state prior to the infection. For these methods, we use the Shadow Copy feature which is included in Windows XP and the latest operating systems (Windows 8, 7 & Vista)
Method 1: Restore Cryptolocker encrypted files using Windows “Restore Previous versions” feature.
Method 2: Restore Cryptolocker encrypted files using Shadow Explorer.
Method 1: Restore Cryptolocker encrypted files using Windows “Restore Previous versions” feature.
How to restore CryptoLocker encrypted files using Windows “Restore Previous versions” feature:
1. Navigate to the folder or the file that you want to restore in a previous state and right-click on it.
2. From the drop-down menu select “Restore Previous Versions”. *
Notice* for Windows XP users: Select “Properties” and then the “Previous Versions” tab.
3. Then choose a particular version of folder or file and the press the:
- “Open” button to view the contents of that folder/file.
- “Copy” to copy this folder/file to another location on your computer (e.g. you external hard drive).
- “Restore” to restore the folder file to the same location and replace the existing one.

Method 2: Restore Cryptolocker encrypted files using Shadow Explorer.
How to restore CryptoLocker encrypted files using “Shadow Explorer” utility.
ShadowExplorer, is a free replacement for the Previous Versions feature of Microsoft Windows Vista/ 7 / 8. You can restore lost or damaged files from Shadow Copies.
1. Download ShadowExplorer utility from here. (You can either download the ShadowExplorer installer or the Portable version of the program).
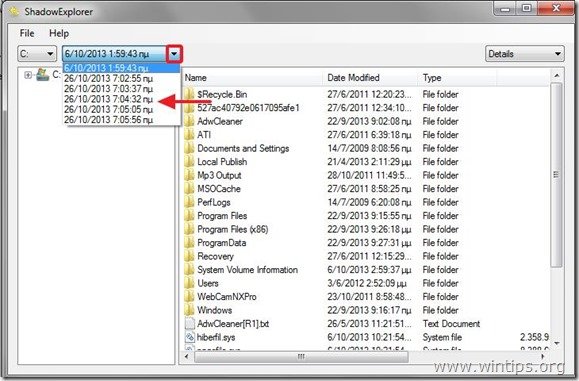
2. Run ShadowExplorer utility and then select the date that you want to restore the shadow copy of your folder/files.
3. Now navigate to the folder/file that you want to restore its previous version, right-click on it and select “Export”
4. Finally specify where the shadow copy of your folder/file will be exported/saved (e.g. your Desktop) and press “OK”
That’s it.
We're hiring
We're looking for part-time or full-time technical writers to join our team! It's about a remote position that qualified tech writers from anywhere in the world can apply. Click here for more details.
- FIX: Numeric keypad Not Working on Windows 10/11 - July 24, 2024
- How to Share Files or Printers in Hyper-V? - July 22, 2024
- How to invoke Hyper-V Screen resolution prompt? - July 17, 2024

![safe-mode-with-networking_thumb1_thu[1] safe-mode-with-networking_thumb1_thu[1]](https://www.wintips.org/wp-content/uploads/2013/10/safe-mode-with-networking_thumb1_thu1_thumb.jpg)


![ShadowExplorer export[5] ShadowExplorer export[5]](https://www.wintips.org/wp-content/uploads/2013/10/ShadowExplorer-export5_thumb.jpg)





May 16, 2017 @ 8:07 am
Ransomware attack making the storage devices inaccessible and there is no specific solution suggested yet by experts which can easily troubleshoot this issue. However, if you have a Windows data recovery software then you can easily recover your files the ransomware affected hard drives.
October 31, 2016 @ 8:54 pm
My Win 7 Pro infected w/ RSA 1024? for some reason to complete steps, admin and administration folders are not there missing..? all files say crypted lost access to internet to download anything its now disconnected can't be used whats next ? frustated
October 16, 2016 @ 10:18 pm
And now I tried to restore my stuff and THERE ARE NO PRECIOUS VERSIONS and Shadow Explorer is also coming up empty. FML
October 16, 2016 @ 9:58 pm
Ugh, I was doing so good until the part about deleting hidden files. I was able to enable the hidden ones, but where do I go to access my files, so that I can delete the hidden dangers? I have Windows 7. Thanks so much for your help.
October 7, 2016 @ 7:11 am
my files are encrypted with ransomeware and extenstentions of my files are change to a3e1 windows 7
October 7, 2016 @ 8:53 am
@thota ajay kumar: I think its a new ransomware and I don't know a method to recover your files. Have you tried to restore your files to previous versions?
August 16, 2016 @ 8:26 am
I have been infected with crypt0l0cker and the locked files end with .enc
Is there any way to decrypt these files?
August 16, 2016 @ 2:45 pm
@Staf: I think that this time there is no way to decrypt .enc encrypted files, but give a try with the RakhniDecryptor.
July 23, 2016 @ 2:10 pm
hello
my labtop infect by RSA4096
. all my data is code and I cannot open them.
I have some data health in back up in another computer.
can fine key with two files (health & damage). do you have soft ware for discovery key and decrypt program.
please email answer to me
July 25, 2016 @ 9:04 am
@sasan: What ransomware it is? Name? In what extension your files are named to?
April 19, 2016 @ 11:22 am
if your shadow copy is enable in your both all drives, but by Default only in local drive c shadow enable. but rest of drive you need to enable shadow, in my case i recovery all my crypt files which on local drive c but most of my data was on local drive d, which is still not recover. if anyone can help me it will be great.
April 2, 2016 @ 11:39 pm
Why are the professional hackers that do good like anomyous blocking these scum of the earth hackers that are attacking innocent family computers, ie robbing the poor to pay the rich, ie generate millions of dollars for chain stores like Staples etc???
March 23, 2016 @ 10:59 am
Hello lakonst,
My formatted disk C/D is no longer encrypted after formatting. I ran Malwarebytes and some other detection software, I think my system is clean. Like what you've mention in your msg, my understanding of recovery software is also that it must first be deleted in order to be recovered. The thing is the files on C/D are not important to me, it's the files on F/G(which have not been formatted and still in encrypted state) that I desperately need. So, since F/G are still in its encrypted state, is my only option to pay?
Thank you so much again , you are the only reply I've been getting so far
March 23, 2016 @ 12:23 pm
@Jon: As I know so far: If you have already cleared your system, you will not be able to recover the encrypted files even if you paid the ransom, so unfortunately you have lost your files :(
March 23, 2016 @ 8:58 am
Thank you so much for a response! I have been spending my time trying to recover F/G, which is where all the important stuffs are. I have not ran recovery on the formatted C/D as there isn't much besides operating system and programs there to begin with. My situation is that I keep important files on F/G and when i need to use the files, I connect F/G to the computer and start working. I will try EaseUS on F/G now, but so far PhotoRec have only been able to pickup useless files on F/G. I'm not sure of the nature of recovery programs, but FYI, I seldom delete things on F/G. My son's photo's for example(which is my main heart break in this situation), I would only save to F/G and seldom delete. If there are any other details you need, please let me know. the clock is counting down for me. Like my previous mentioned msg, Im borderline ready to pay, but having formatted C/D, will this have an affect on the decrytopn process? Thank you so much!
March 23, 2016 @ 10:39 am
@jon: Hello Jon. The data recovery programs only recover missing (deleted-formatted) files, they don't decrypt files. Is your formatted disk also encrypted? If it is encrypted, then probably you couldn't be able to recover your files. If it is not encrypted, I suggest to install the "Easeus" recovery program to another clean computer. After installation connect the formatted disk on it and try to recover files.
March 22, 2016 @ 1:30 pm
Hello, I was hit with rsa 4096 about 2 days ago. Had just formatted my C/D drives and was downloading some programs back onto the computer. Made a mistake of downloading something unfamiliar… and the reason im here is because after everything was encrypted, in a rush and not knowing the nature of this malware, i formatted my main disk, and i did it without thinking that my other disk drive may be affected already. So what i have now, is a formatted disk drive C and D, and an encrypted disk drive F and G. No files showed with Shadow explorer, im trying different recovery software and its picking up some old files that i deleted but not the files i need. Im still trying but at this point im ready to pay, and my main concern is can i still decrypt after having formatted the main disk? Thank you all!
March 22, 2016 @ 4:33 pm
@jon: You have tried the EaseUS Data Recovery on the formatted disk??
June 14, 2015 @ 10:44 am
Do you have other recovery system than both of these?
I tried both of this but it doesn't work.
Please help.
June 14, 2015 @ 12:47 pm
@Jia: Unfortunately I haven't.
May 25, 2015 @ 10:37 am
This virus or whatever it is it wants to delete 2000 files that i have got. They include my Sims games which are kind of important to me. My question is: What do i use to delete the Cryptolocker Hidden files? I have Windows 8 and it's not written if I can use it on Windows 8.
May 25, 2015 @ 2:55 pm
@Lisa: You can use the same instructions for Win8.
April 20, 2015 @ 4:31 am
Hi I got this malware 2 days ago, I cleaned up my computer but I can decrypt my files. So I decided to transfer my decrypted files to my external hardrive but while transferring I saw this text file that was named RECOVERY_KEY.TXT I was wondering what is this? I don't know if this is the key to recover my files? what do you think?
Here are the things in that text when I click this file:
1LnZxy5kbLomVQP6v92UYHwPCPcQppWCCa
03E8C1CDB6A42F8F434F3D158B733031F96C9C9A5247C7D9C0367A56EBFFDE11
4CDBE7366FFA75CD6AA0FE46766DB18AECA258A84DC7E4A05D9A1FB1D7515F6E014D6D3BC4D004024C14B0E5A103529A44471FB1242C16158A5BC1BBBB680B3C
what does this mean?
April 20, 2015 @ 9:27 am
@krisshir: RECOVERY_KEY.txt is a file created by the TeslaCrypt or by the Cryptowall virus. I don't think that this file contains the key to recover your files and as I know (until today) there is no a decryption way to get your files back.
September 21, 2016 @ 4:20 am
lakonst,
I seen on McAfee's website, under the " for enterprise" category, then on the top of the page click on "support" link then click on Product Download link…
Then on that page there is a section for "see all Free Tools"…
Within this page, there is a decryptor tool called "Tesladecrypt"
Download this tool, this will remove the crypto version that you are stating that you have, HOWEVER… you will need to still have the message on your screen to get some key information that this decryptor will need or have access to the crypto files on your computer to get the information you need.
But also there are other decryptor tools on McAfee's website, as well… hope this helps! Let me know how it goes for you?
April 23, 2015 @ 6:37 pm
krisshir, I had the exact same thing happen on the same day. I also saved the RECOVERY_KEY.TXT file in the hope that it might contain the decryption key. But I already removed the malware — do you know which one it was? Also: lakonst, why do you think this TXT file does not contain the key?
April 23, 2015 @ 7:44 pm
@jrc: I 'm not sure and I don't know a way to find it out!
April 23, 2015 @ 8:19 pm
At least one of these ransomware/malware programs has a known bug that causes it to leave the decryption key on the user's computer:
http://www.pcworld.com/article/2138300/mistake-in-ransomware-program-leaves-decryption-key-accessible.html
So I thought this might be the same thing. The problem is how to test it, without knowing for certain what encryption was used. But look at that txt file that krisshir posted. If it's like mine, the first line is the bitcoin address for payment, and the rest is in hexadecimal. The last two lines (1 long wrapped line) line might be a 1024-bit key?
April 24, 2015 @ 8:17 am
Yes it might! But I haven't an example (encrypted file) to test it and I don't know a decrypt tool to test it.
April 24, 2015 @ 4:03 pm
lakonst, I could send you all the encrypted file examples you want. So could thousands of other people out there. But first we need to figure out what encryption method this malware used. The "big red box" on my screen said RSA-2048 was used, but that isn't necessarily true.
If (as you say) the txt file points to TeslaCrypt or CryptoWall, don't they use AES? (I already sent files to FireEye and they said it was not CryptoLocker.)
April 13, 2015 @ 1:35 pm
Hi! I can't delete the C:\WINDOWS\system32\msctfime.ime. It says to ask permission to TrustedInstaller. What should I do?
April 15, 2015 @ 9:36 am
@Jennifer: Run in safe mode with networking the Norton Power Eraser tool.
April 8, 2015 @ 10:11 pm
Hi today 4/8/2015 i has infected for CryptoLocker i clear the mallware but y loock all my files i dont open the first think i wacht the date the virus modify both dates some body help me please
April 9, 2015 @ 7:36 am
@Victor Julio: Using shadow explorer. restore the files back. If shadow explorer doesn't show other dates, this means that System Restore was disabled in your computer. In that case the only way to get your files back is from a clean backup (if you have one).
March 4, 2015 @ 3:18 am
I have tried both method and failed. i did use shadow exploere but i couldnt get any dates outside the affected date.
Will formatting the computer will completely erasing the cryptowall. I think i will be heading to that path and losing so much photos memories of my kid.
February 25, 2015 @ 1:24 am
Este programa salvou minha vida “Shadow Explorer”
February 21, 2015 @ 8:56 pm
I have windows 8.1 and im having trouble starting my laptop up with safemode, when i press F8 the booting options doesnt appear
February 22, 2015 @ 2:25 pm
@Taysheona: To boot Windows 8 to Safe mode:
– At the login screen: Hold down the SHIFT key while clicking on Power > Restart. Then follow the instructions from here.
February 18, 2015 @ 2:28 am
Is it the same process on windows 8.1?
February 18, 2015 @ 10:01 am
@Taysheona: Yes it is.
February 16, 2015 @ 4:30 am
the machanism detects the file but does not repair them please help send me an mail, the code is RSA 1024 i I have no idea how to fix it please help
February 4, 2015 @ 3:30 pm
Hi, I had some files encrypted by ransom ware on my common shared folder, but when I try to run shadow explorer on the system where the drive is stored its giving me an error saying Cannot start service from the command line or debugger. A windows Service must first be installed(using installutil.exe) and then started with the ServerExplorer, Windows Services Afministrative tool or the NET START command.
February 5, 2015 @ 12:41 pm
@vinesh: Check in Windows services if the "Volume Shadow Copy Service" is started.(Change the Startup type to Automatic & restart the computer)
January 26, 2015 @ 7:01 am
Is it save to backup data to a clean USB while off-line?
January 27, 2015 @ 10:14 am
No, it is not! You have to clean your computer first!
November 10, 2014 @ 11:06 pm
Is there a way to get quickbooks through shadow explorer? I thought I had system restore setup but I do not and quickbooks does not have a recent backup. Shadow explorer seems to be working on the files I have attempted, however I do not have the option to use it on here.
Thanks!
June 18, 2014 @ 9:54 am
Kaspersky XoristDecryptor — this works for the error message below:– it decrypts and creates new files of all the locked files….
Your files are locked and encrypted with a
unique RSA-1024 key!
To regain access you have to obtain the
private key (password).
++++++++++++++++++++
To receive your private key (password):
Go to ht**tp://u5ubeuzasamg54x5f3.onion.to
and follow the instructions.
You will receive your private key (password)
within 24 hours.
Your ID# is 28403489
If you can't find the page, install the Tor
browser (ht**tps://www.torproject.org/
projects/torbrowser.html.en ) and browse to
ht**tp://u5ubeuzasamg54x5f3.onion
++++++++++++++++++++
BEWARE – this is NOT a virus.
The ONLY way to unlock your files/data is
to obtain your private key (password) or
you may consider all your data lost.
You have just 5 days before the private key
(password) is deleted from our server,
leaving your data irrevocably broken.
++++++++++++++++++++
LOCKED ON POSSESSION OF COPYRIGHTED
MATERIAL AND SUSPICION OF
(CHILD)PORNOGRAPHIC MATERIAL.
June 5, 2014 @ 12:59 am
I always do a regular backup to a DVD ROM this way a virus cannot infect your read-only backup unlike with an external drive.
May 27, 2014 @ 12:43 pm
I had windows 7 when my computer infected by " cryptolocker " . I re installed a new windows 7 and removed the " cryptolocker " by antivirus scanning . But my files remains locked . I have no back up from my files . I tried to follow your orders here but I couldn't re back my files . I installed " ShadowExplorer " but when I choose any drive which have locked files it doesn't show any file or folder . It just shows drive c which contains only windows files and folders whiles my locked files are in other drives not in c drive !
May 27, 2014 @ 3:37 pm
Unfortunately you cannot restore files from drives where system protection has not been activated.
April 9, 2014 @ 11:53 am
I have been unable to delete C:\WINDOWS\system32\msctfime.ime from my Windows XP computer even using the application Unlocker or by trying from a command line after killing explorer.exe. I have administrator rights. I have seem that this file may be part of a Microsoft Application (Microsoft Text Frame Work Service IME). Here is one of the pages that white-lists this file. I have cleaned my computer from Cryptolocker, but this msctfime.ime still exists on the PC. Do I need to delete this file?. If so, how as I have been unsuccessful.
April 10, 2014 @ 7:33 am
Hello csiegel, go to https://www.virustotal.com/ & upload/scan this file for risks. If the file is safe no more action is needed. If it is not, then contact me again.
March 7, 2014 @ 10:32 pm
For people using Windows XP. Is it possible to upgrade to Windowss 7 and then use the ShadowExplorer software and try to recover files?
May 27, 2014 @ 6:27 pm
Hi resc2013. I wouldn't advise "upgrading to Win 7", since MS only allows XP to Vista upgrading (Win 7 requires full OS installation).
But if you're looking to access the suggested "previous versions" tab on XP there are two things you'll need to know: 1) if it's a standalone XP machine, XP doesn't have support for volume shadow copy/previous versions; 2) if the XP machine is connected to a network server as a shared drive, you (or your IT admin) can set it up to get previous versions.
March 5, 2014 @ 10:08 am
I successfully did all 4 steps but at 5 step i am not able to recover my files. I have window 7. Please advice soon
March 5, 2014 @ 10:16 am
I 'm afraid that System Restore feature was disabled on the infected computer so you cannot restore your files back.
March 5, 2014 @ 10:31 am
Thank you for your quick reply. I think you are right. But now what i do with my files (.xlsx,.jpg,…) how can I get them back.
March 6, 2014 @ 12:53 pm
Unfortunately you cannot. It is still not possible to decrypt files encrypted by CryptoLocker without paying the ransom.
February 21, 2014 @ 12:48 pm
I have xp pro will anything work for it???
February 23, 2014 @ 11:51 am
Unfortunately there is no method to restore your files in Windows XP.
February 20, 2014 @ 1:33 am
Good info, too bad one of my recent customers had a "little" problem with many different trojan/malware/spyware infections on her laptop, making it impossible to use restore point before cleaning the computer. Also she created one very important document after her machine got infected with cryptolocker, thus making it impossible to look for a clean shadow copy.
Now that's what you call a bad luck…
February 19, 2014 @ 3:27 am
This definitely saved one of my clients' data. Method 1 didn't work, but Method 2 worked like a charm.
January 21, 2014 @ 7:00 pm
my files are neither restored nor decrypted
its windows 7
January 21, 2014 @ 7:31 pm
Probably System Restore was disabled on your system.
January 5, 2014 @ 6:51 am
Thanks !
Good presentation . it was very easily understand .
December 27, 2013 @ 9:34 am
Both methods of Files recovery do not work on Windows 7.
December 25, 2013 @ 4:57 am
after HOURS talking to various microsoft "tech" reps… this site was the only thing that helped and restored files. Microsoft actually told me it was impossible to restore. HA. THANK YOU THANK YOU THANK YOU!!!!
December 20, 2013 @ 2:13 am
This is the first site that actually gives hope in recovering files encrypted by RansonCrypt.F Thanks!